OCI-Based Artifacts
Quay can be used to store OCI-based artifacts like Helm charts, encrypted container images, signed images, zstd compressed images, etc.
Working with Helm Charts
-
Login to the Quay registry with helm.
helm registry login ${QUAY_HOSTNAME}-
Pull a chart.
-
Push the chart into the Quay repository.
helm push quarkus-0.0.3.tgz oci://${QUAY_HOSTNAME}/olleb/helm-
Open the Quay Dashboard and navigate to the
olleb/helm/quarkusrepository. Then, go toTags.
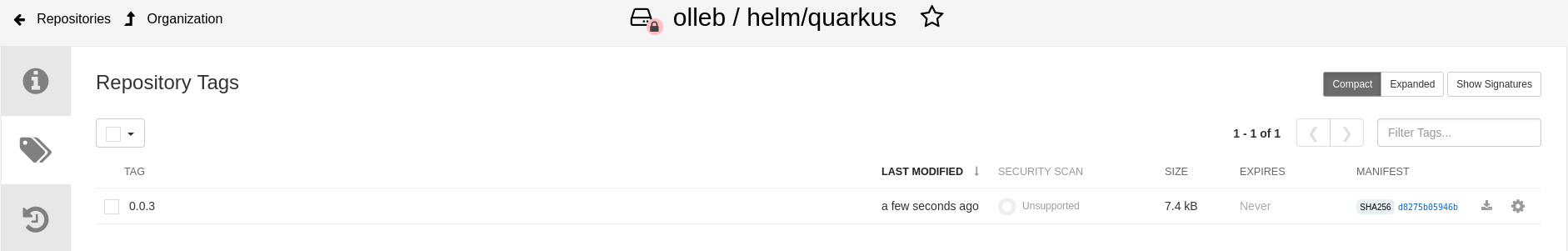
The Helm chart is published to Quay as an OCI image.
-
The Helm chart can now be installed directly from the repository.
helm install quarkus oci://${QUAY_HOSTNAME}/olleb/helm/quarkus --version=0.0.3Signed Container Images
Image signing ensures the integrity and authenticity of image deployments. Quay stores the signature as an OCI artifact.
Signing Container Images with Cosign
-
Generate a key pair.
cosign generate-key-pair-
Sign an image and push it to Quay.
# Pull the image
podman pull quay.io/fedora/httpd-24-micro:2.4
# Tag and push the image
podman tag quay.io/fedora/httpd-24-micro:2.4 ${QUAY_HOSTNAME}/olleb/httpd-24-micro:2.4
# Log in
podman login ${QUAY_HOSTNAME}
# Push the image
podman push ${QUAY_HOSTNAME}/olleb/httpd-24-micro:2.4
# Log in with cosign
DOCKER_CONFIG="${XDG_RUNTIME_DIR}/containers/" cosign login ${QUAY_HOSTNAME} -u <USER>
# Sign and push the signature
DIGEST=$(podman inspect --format '{{.Digest}}' "${QUAY_HOSTNAME}/olleb/httpd-24-micro:2.4")
cosign sign --key cosign.key "${QUAY_HOSTNAME}/olleb/httpd-24-micro@$DIGEST" --tlog-upload=false-
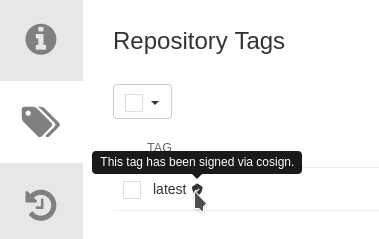
Navigate to the Quay Dashboard and open the
olleb/httpd-24-microrepository. -
Click
Tags.
You should now see the signature stored in the repository.
Signing Container Images with PGP (RFC4880)
-
Generate PGP keys.
gpg --batch --gen-key <<EOF
Key-Type: RSA
Key-Length: 4096
Name-Real: Angel
Name-Email: [email protected]
Expire-Date: 0
%commit
EOF-
Sign the image and push it to Quay.
podman push --sign-by [email protected] ${QUAY_HOSTNAME}/olleb/httpd-24-micro:2.4 --tls-verify=falseThe signature can be verified with:
gpg --verify ~/.local/share/containers/sigstore/olleb/httpd-24-micro@sha256=<SHA>/signature-1
skopeo can also be used for signing and moving images between registries.
|
Encrypted Container Images
An image can be encrypted using one or more keys. You can encrypt the entire image layers or specific layers. In any case, the container image can be stored in Quay.
Encrypted images are used to protect private and sensitive content in your images, for example, in case the registry is compromised.
Typically, the image decryption key is stored in a secret on the OCP cluster master node.
Encrypting Container Images with JSON Web Encryption (JWE) (RFC7516)
-
Generate RSA encryption keys using OpenSSL.
# Private key
openssl genrsa --out private-key.pem 2048
# Public key
openssl rsa -in private-key.pem -pubout -out public-key.pem-
Pull the image you want to encrypt.
# Pull the image
podman pull quay.io/fedora/mysql-80:80
# Tag and push the image
podman tag quay.io/fedora/mysql-80:80 ${QUAY_HOSTNAME}/olleb/mysql-80:jwe-
Encrypt and push the image.
podman push --encryption-key jwe:public-key.pem ${QUAY_HOSTNAME}/olleb/mysql-80:jwe-
Navigate to the Quay Dashboard and open the
olleb/mysql-80repository. -
Click
Tags.
You will see the encrypted image stored in the repository.
podman inspect ${QUAY_HOSTNAME}/olleb/mysql-80:jweTry pulling it with:
# Remove the local image if it exists
podman rmi ${QUAY_HOSTNAME}/olleb/mysql-80:jwe
# Pull
podman pull ${QUAY_HOSTNAME}/olleb/mysql-80:jweYou will get an error like Error: writing blob: layer 0 (blob "sha256:….
Now, pull the image providing the private key for decryption:
podman pull --decryption-key private-key.pem ${QUAY_HOSTNAME}/olleb/mysql-80:jweThe image will be pulled without issues.
skopeo can also be used to perform the same steps.
|
Encrypting Container Images with PGP (RFC4880)
-
Generate PGP keys.
gpg --batch --gen-key <<EOF
Key-Type: RSA
Key-Length: 4096
Name-Real: Angel
Name-Email: [email protected]
Expire-Date: 0
%commit
EOF-
Pull the image you want to encrypt.
# pull the image
podman pull quay.io/fedora/postgresql-16:16
# tag and push the image
podman tag quay.io/fedora/postgresql-16:16 ${QUAY_HOSTNAME}/olleb/postgresql-16:pgp-
Encrypt and push the image.
podman push --encryption-key pgp:[email protected] ${QUAY_HOSTNAME}/olleb/postgresql-16:pgp-
Navigate to the Quay Dashboard and open the
olleb/postgresql-16repository. -
Click
Tags.
You will see the encrypted image stored in the repository.
skopeo can also be used to perform the same steps.
|