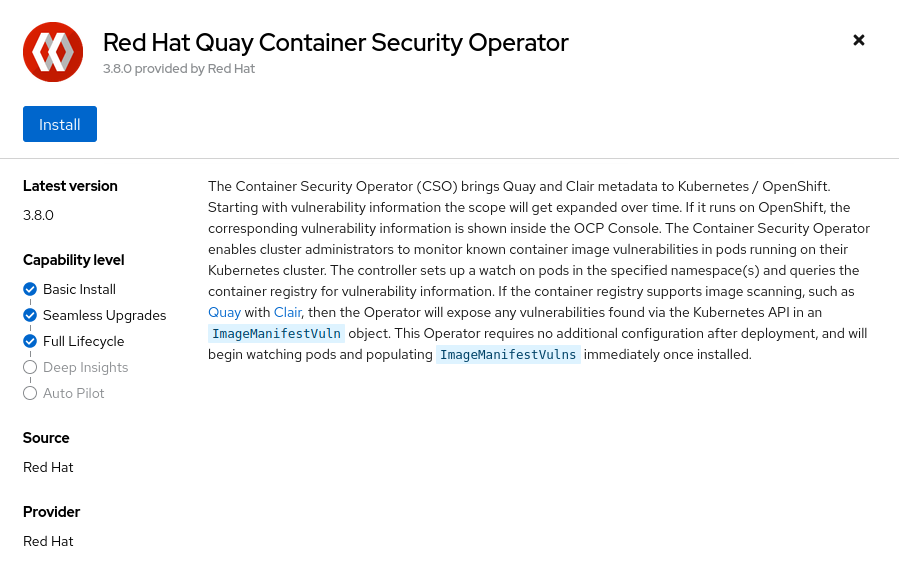
Container Security Operator (CSO)
Scan pod images using the Red Hat Quay Container Security Operator (CSO).
The Container Security Operator integrates Quay and Clair metadata into Kubernetes / Red Hat OpenShift, allowing you to scan images for vulnerabilities and compliance issues. This ensures that the images used in your pods are secure and meet relevant standards.
Installing the Quay CSO Operator
-
Open a browser and log in to the Red Hat OpenShift Container Platform web console.
-
From the Administrator perspective, click
Operatorsand thenOperatorHub. -
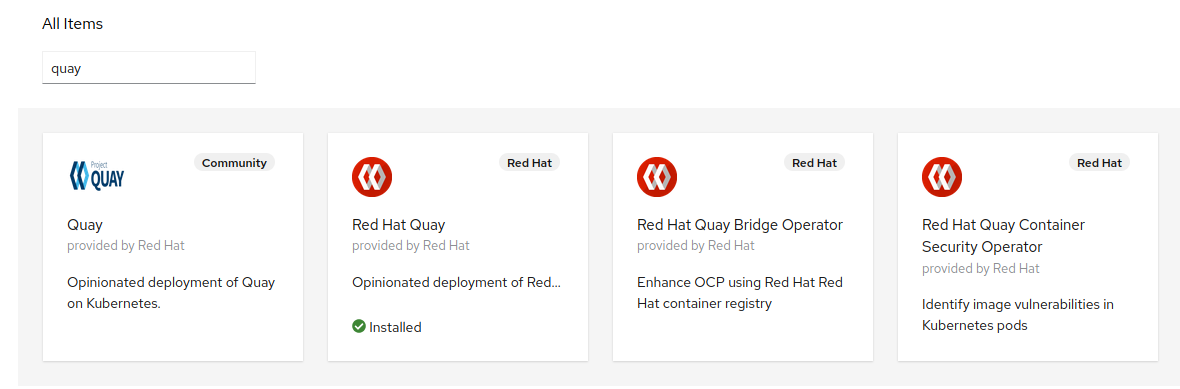
In the
Filter by keywordfield, typeRed Hat Quay.
-
Select the
Red Hat Quay Container Security Operatortile and clickInstall.
-
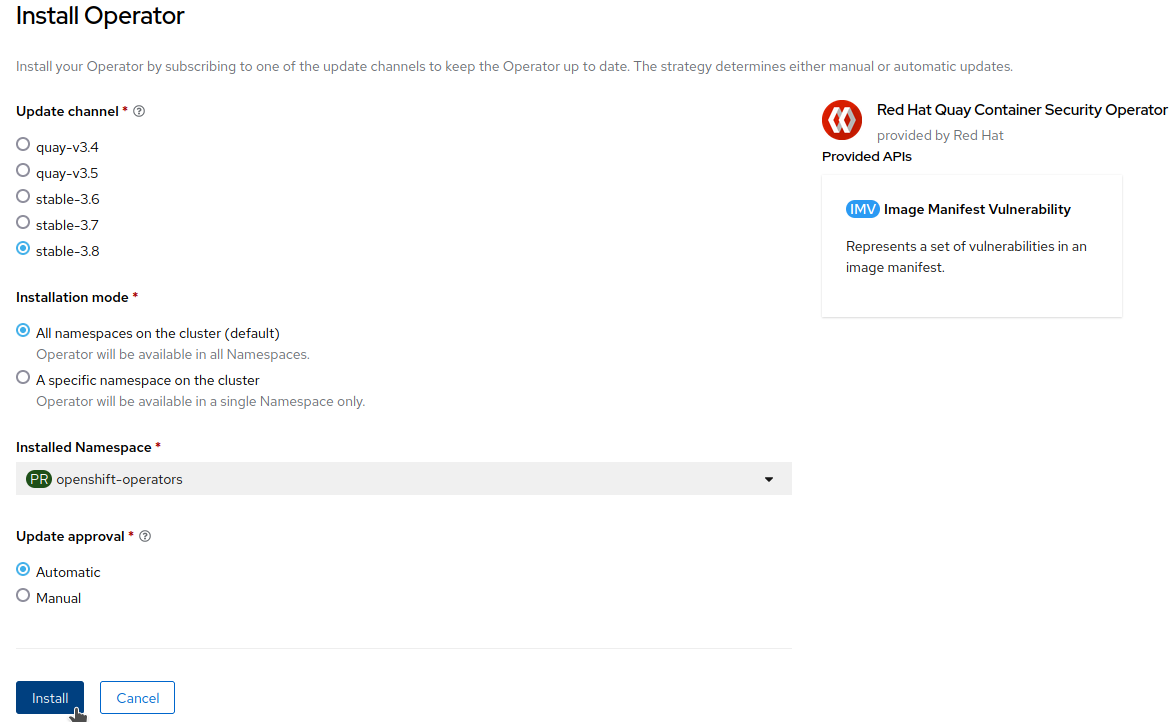
On the
Install Operatorpage, selectstable-3.15from theUpdate Channeloptions. ChooseAll namespaces on the cluster (default)as the installation mode and selectAutomaticfor update approval.
-
Click
Installto start the installation.
Checking Image Vulnerabilities from the Red Hat OpenShift Web Console
Deploy a vulnerable image to verify how the Quay Container Security Operator (CSO) detects and displays image vulnerabilities in the OpenShift console.
-
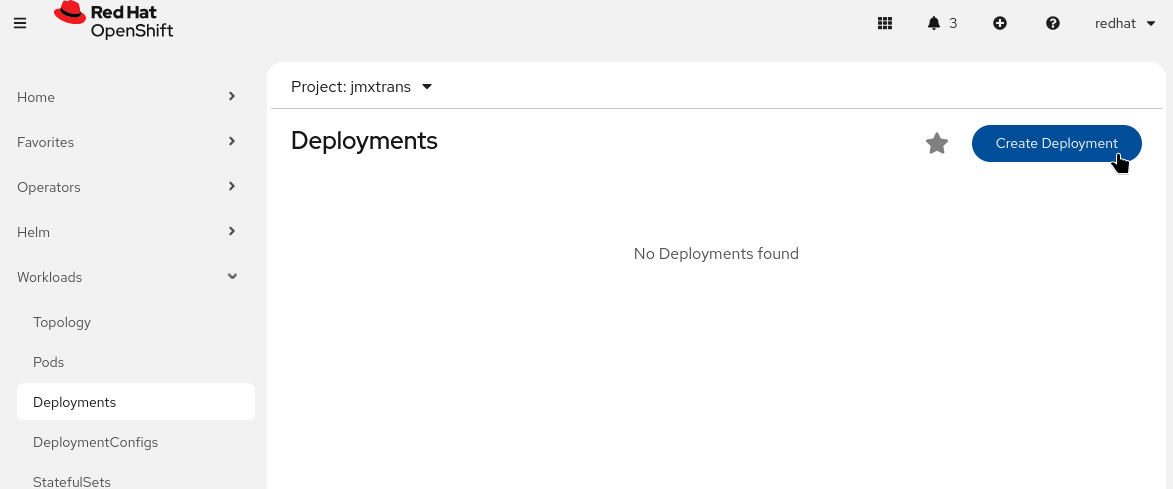
Open the Red Hat OpenShift Container Platform web console and create a new project by clicking
Projects, thenCreate Project. Name the projectjmxtransand clickCreate. -
With the
jmxtransproject selected, deploy the vulnerable image by clickingWorkloads, thenDeployments. ClickCreate Deployment.
-
Switch to
YAML viewand replace the default image value with the image from your Quay registry. Set the number of replicas as desired, and name the deploymentjmxtrans.
apiVersion: apps/v1
kind: Deployment
metadata:
namespace: jmxtrans
name: 'jmxtrans'
spec:
selector:
matchLabels:
app: name
replicas: 1
template:
metadata:
labels:
app: name
spec:
containers:
- name: container
image: >-
quay.io/strimzi/jmxtrans:0.34.0
ports:
- containerPort: 8080
protocol: TCP
strategy:
type: RollingUpdate
rollingUpdate:
maxSurge: 25%
maxUnavailable: 25%-
Click
Create. -
Red Hat OpenShift will start the deployment and create the pod. Go to
Workloads→Podsand select one of thejmxtranspods. Then open theVulnerabilitiestab.
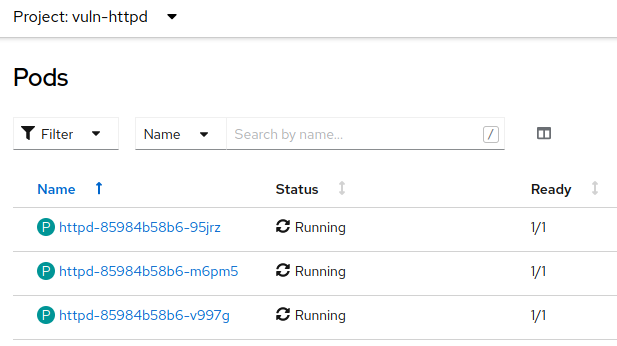
-
Click any listed vulnerability to open its details.
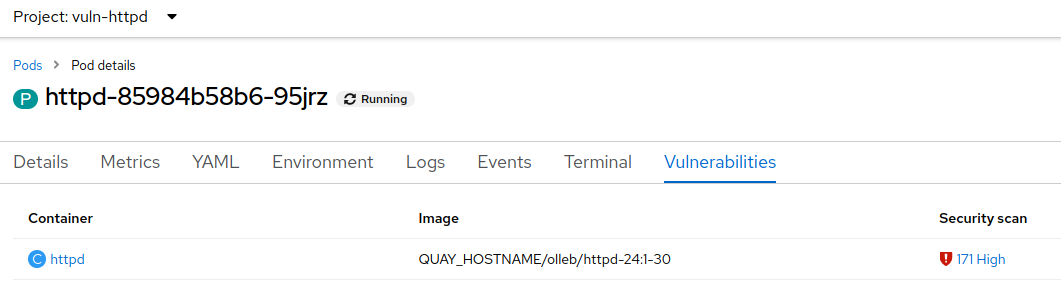
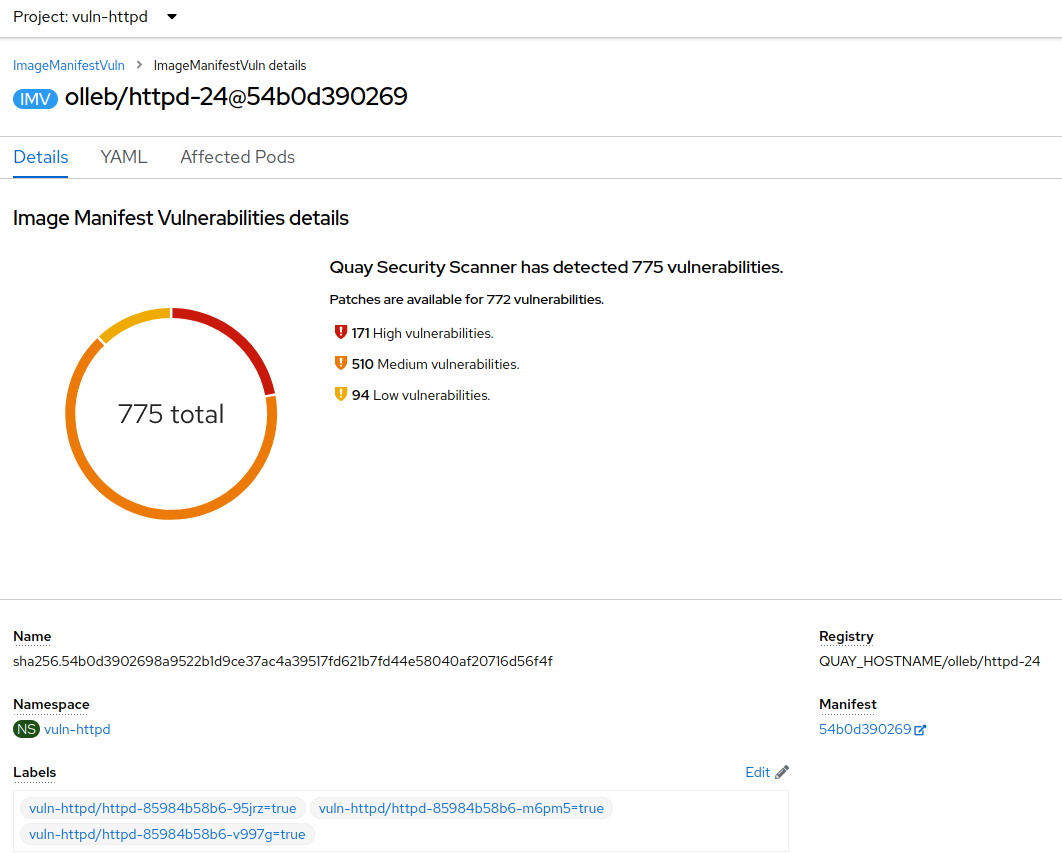
You will see the Image Manifest Vulnerabilities view:
Additionally, after installing the CSO Operator, a new Image Vulnerabilities status appears on the Cluster Overview page.
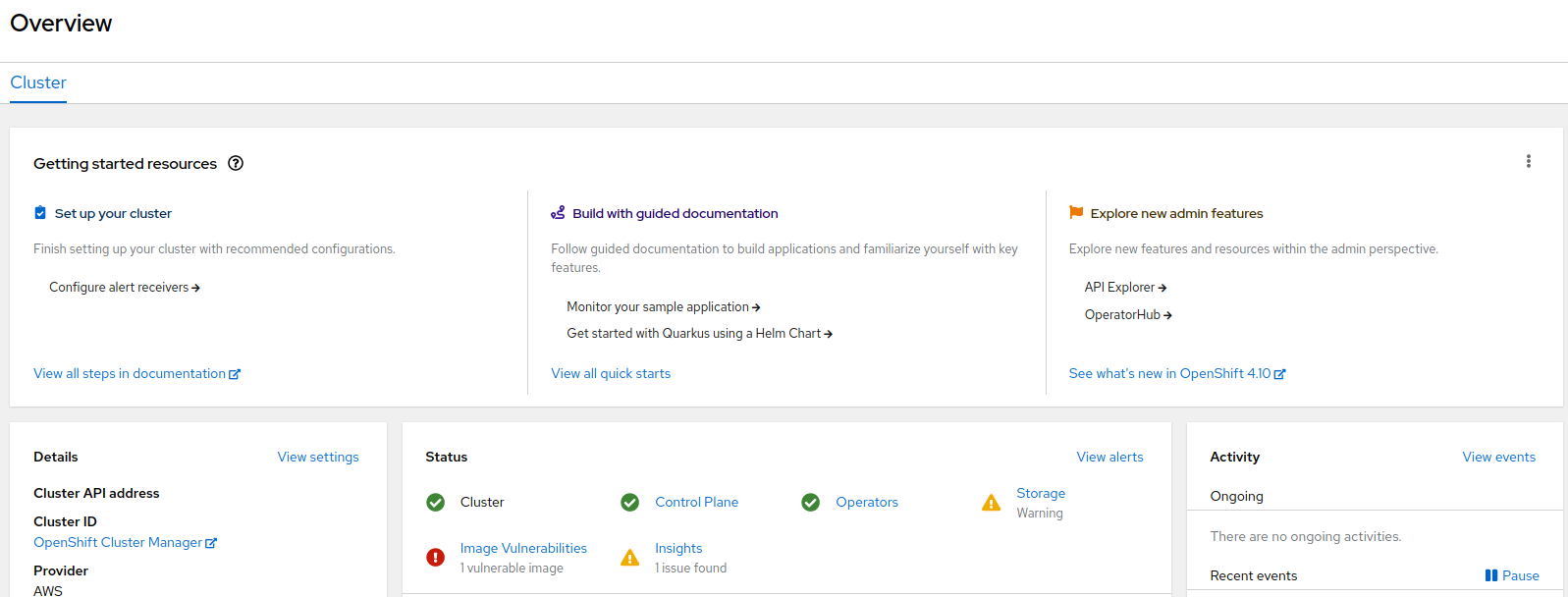
-
Click
Image Vulnerabilities, thenView all, and filter by thejmxtransproject.
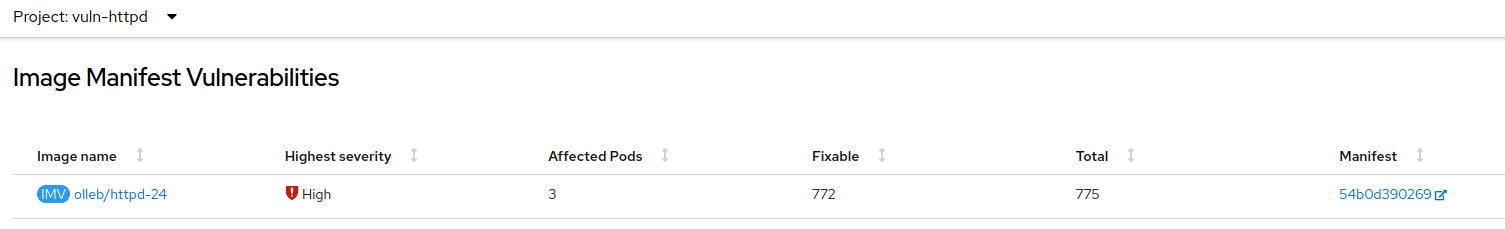
-
Click on a specific manifest entry to view more details. You will be redirected to the Quay Security Scanner Dashboard.
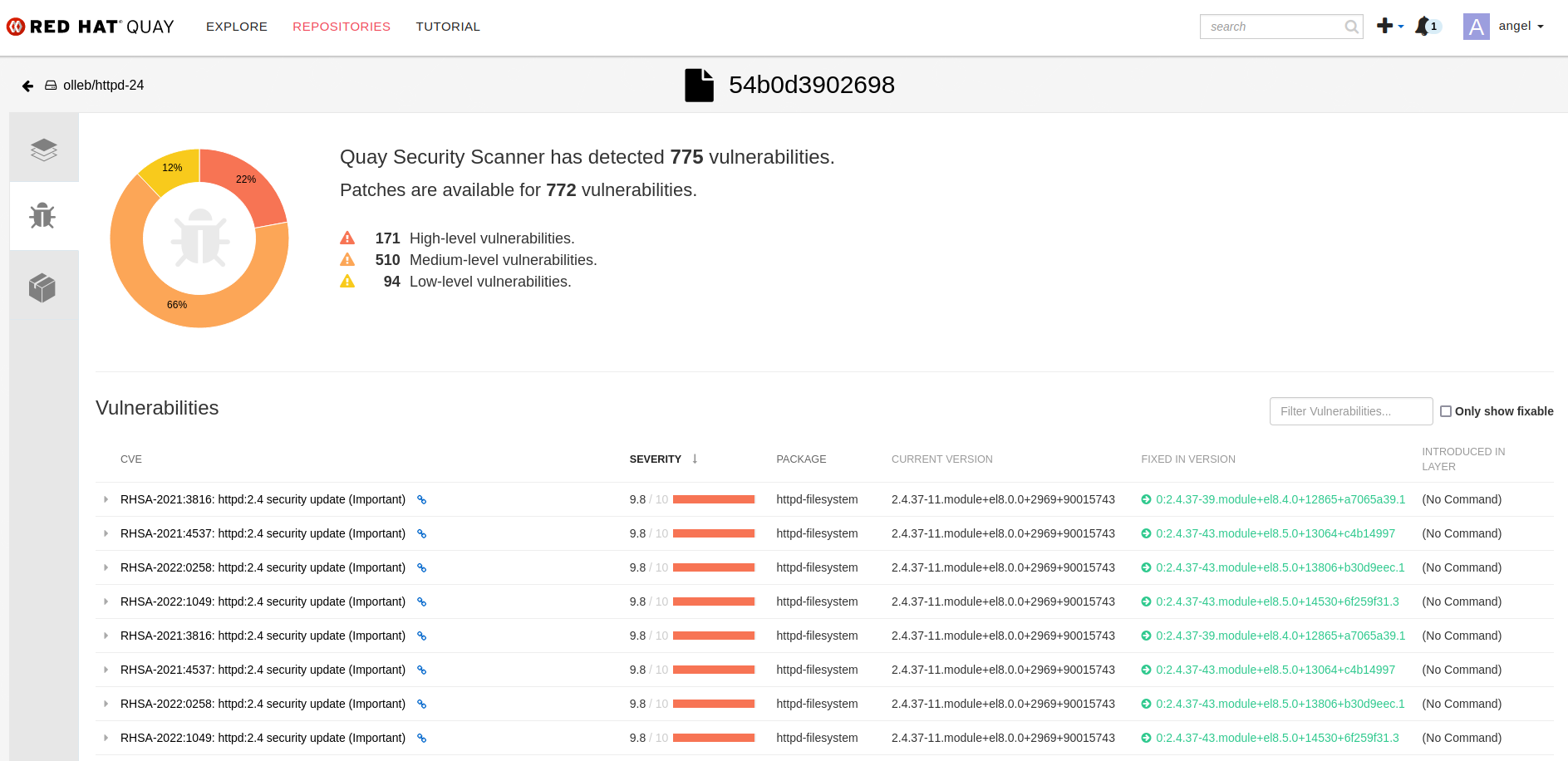
By integrating the Red Hat Quay Container Security Operator (CSO) with OpenShift, we can automatically surface image vulnerabilities directly in the cluster console.
This integration bridges image scanning data from Quay and Clair with running workloads, enabling proactive detection and remediation of vulnerabilities across deployed containers.