Secrets and Vault Integration
Vault SPI
The Vault SPI enables the creation of custom extensions for Red Hat Single Sign-On (RH-SSO) that integrate with any external vault implementation.
Using the Vault SPI, RH-SSO can securely retrieve secrets—such as passwords, keys, or tokens—from the vault of your choice, providing a flexible and centralized way to manage sensitive data.
Integrating RH-SSO with Conjur using the Vault SPI
This chapter explains how to integrate Red Hat Single Sign-On (RH-SSO) with Conjur using the Vault SPI. For this demo, we will retrieve the 389 Directory Server credentials of the cn=Directory Manager user stored in Conjur, which will be used by RH-SSO for user federation.
-
Run the provided Conjur OSS community collection included in this workshop.
-
Create the admin account
demoAccount:
conjurctl account create demoAccount > /tmp/admin_dataThe admin_data file contains the public key and API key of the admin user.
-
Load the provided Conjur policy and create a secret for the demo:
APIKEY=$(sed -n '/API/ s/.*: *//p' /tmp/admin_data)
TOKEN=$(curl --header "Accept-Encoding: base64" -d $APIKEY https://$CONJUR_HOST/authn/demoAccount/admin/authenticate)
curl -H "Authorization: Token token=\"${TOKEN}\"" -d "$(< policy.yml)" https://$CONJUR_HOST/policies/demoAccount/policy/root
curl -H "Authorization: Token token=\"${TOKEN}\"" -d "password" https://$CONJUR_HOST/secrets/demoAccount/variable/ldap/password| We are using the REST API here, but other approaches like the Conjur CLI can also be used. |
-
Export the required environment variables for the Vault SPI:
export CONJUR_ACCOUNT=demoAccount
export CONJUR_AUTHN_API_KEY=$APIKEY
export CONJUR_APPLIANCE_URL=https://$CONJUR_HOST
export CONJUR_AUTHN_LOGIN=adminAlternatively, the SPI provider properties can be configured directly instead of using environment variables.
-
Deploy the extension and configure the Vault SPI in RH-SSO:
/subsystem=keycloak-server/spi=vault:add
/subsystem=keycloak-server/spi=vault/provider=conjur-vault:add(enabled=true)
/subsystem=keycloak-server/spi=vault:write-attribute(name=default-provider,value=conjur-vault)
:reload-
Ensure the 389 Directory Server is running and that the Conjur extension and Vault SPI are configured.
</dev/tcp/<389_HOST>/3389-
Log in to the RH-SSO administration web console.
-
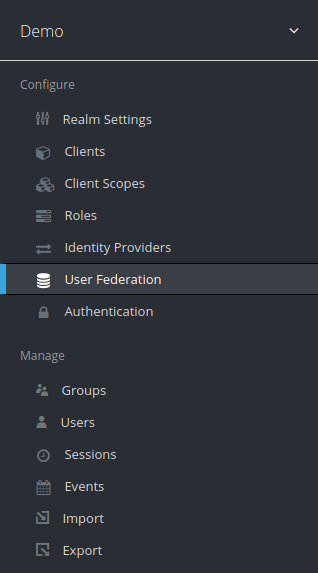
Select the
Demorealm and clickUser Federation.
-
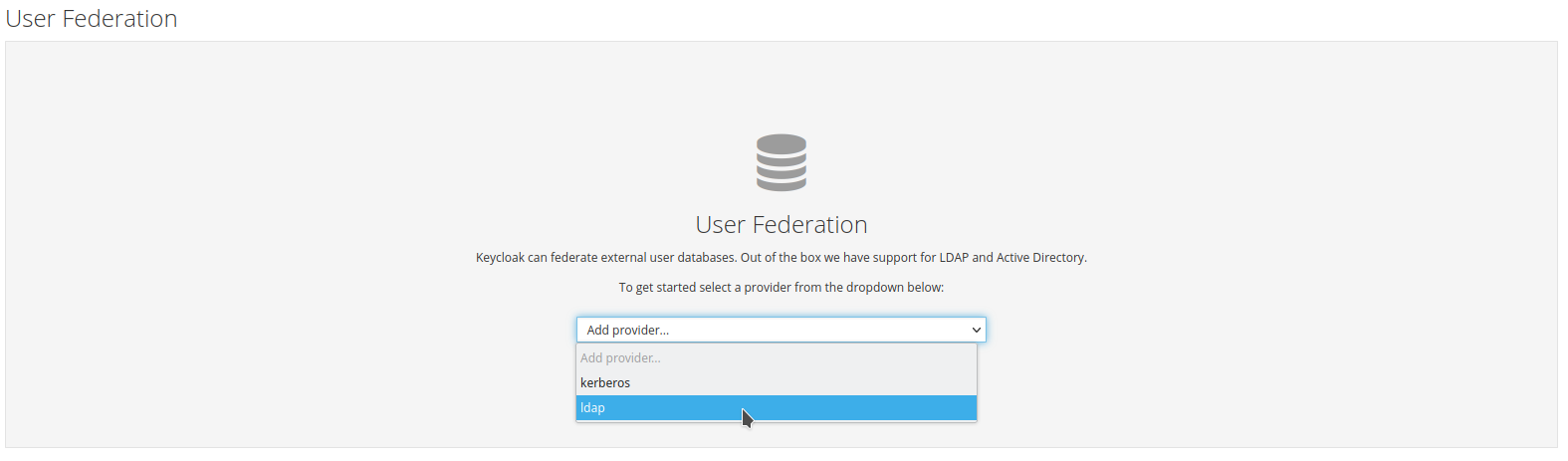
Select
ldapas the provider.
-
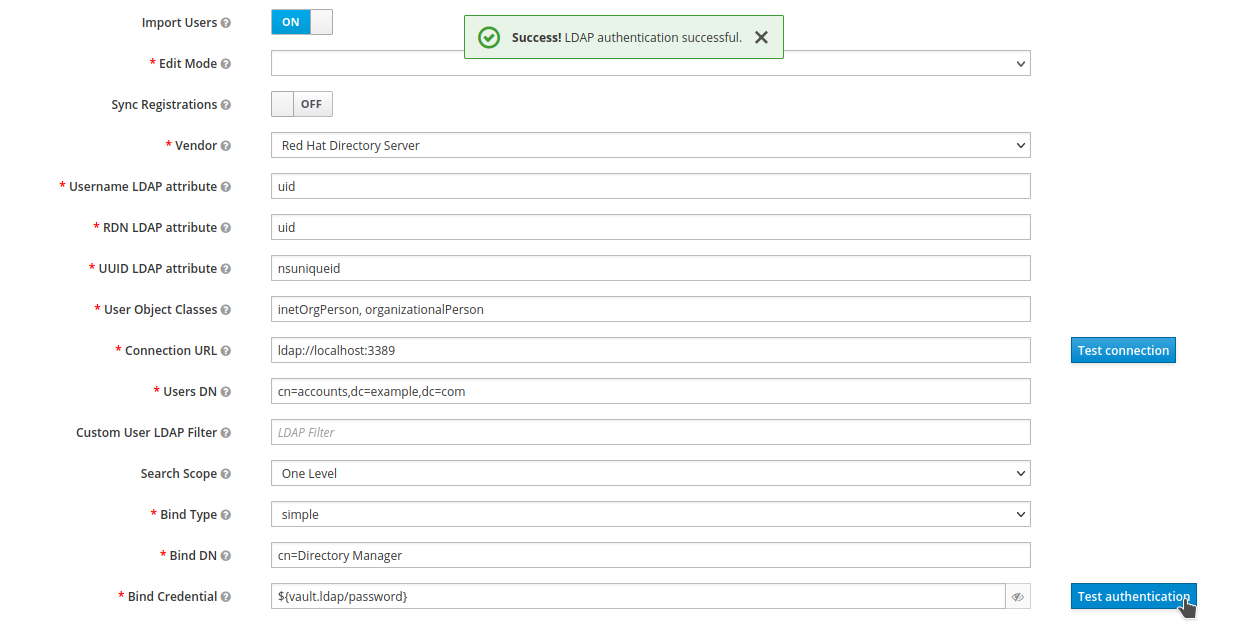
Fill in the LDAP provider settings. Click
Test connectionto verify connectivity. A successful test will show:
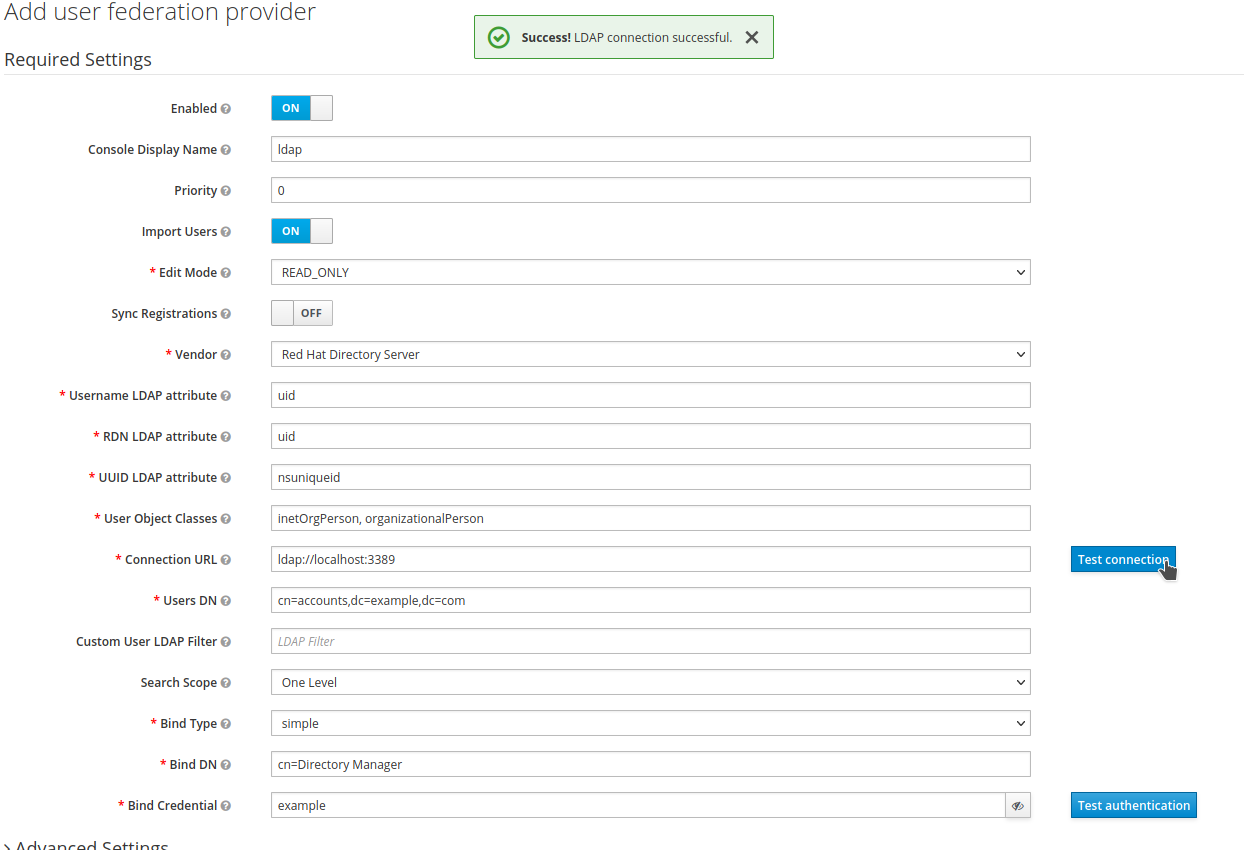
-
Test authentication with a wrong password. It should fail:
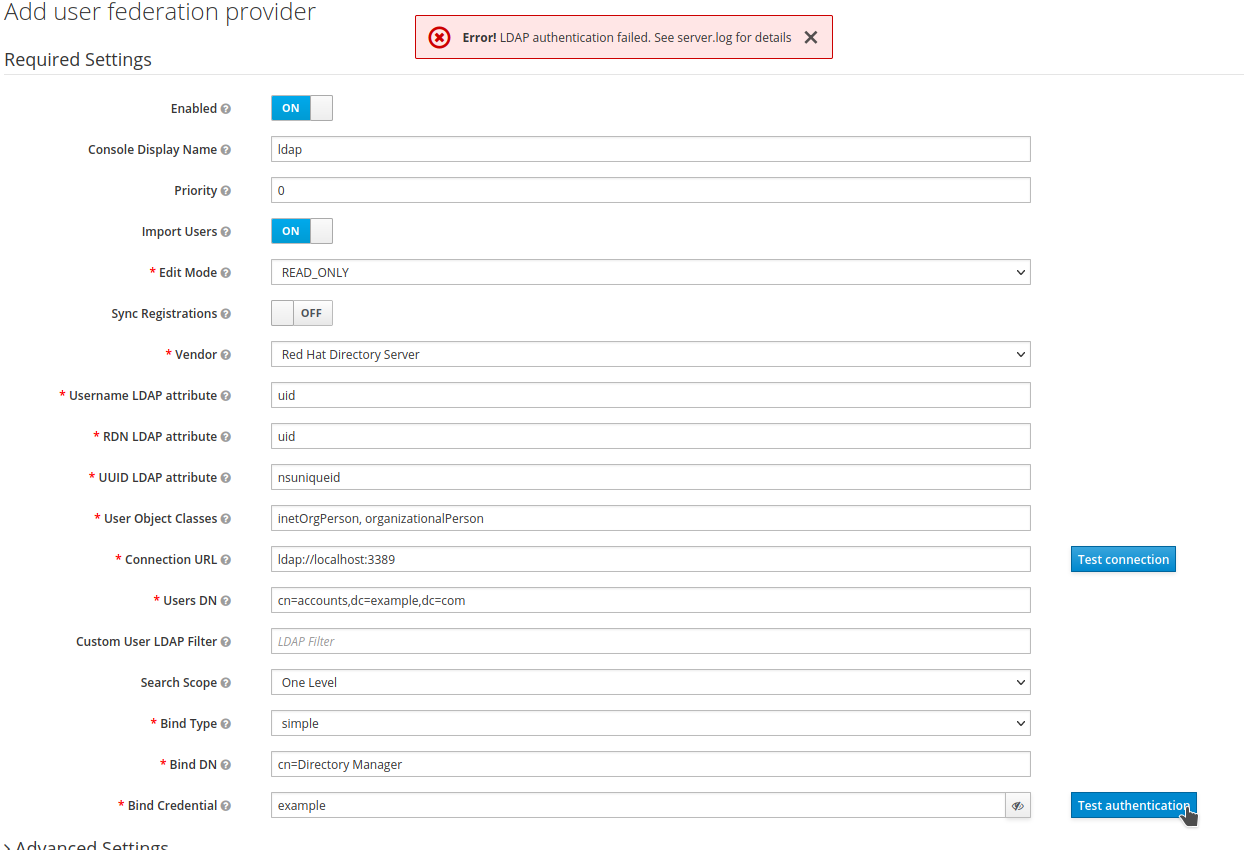
-
Set the
Bind Credentialto the vault value${vault.ldap/password}. Test authentication again. It should succeed: