User Federation
LDAP User Federation
Red Hat Single Sign-On (RH-SSO) can validate credentials from LDAP or Active Directory. In this section, we will integrate RH-SSO with IdM/FreeIPA.
Creating a user in FreeIPA
-
Open the FreeIPA administration web console.
-
Create a new user
robert: -
Browse to
Identity→Users. -
Click
Add.
-
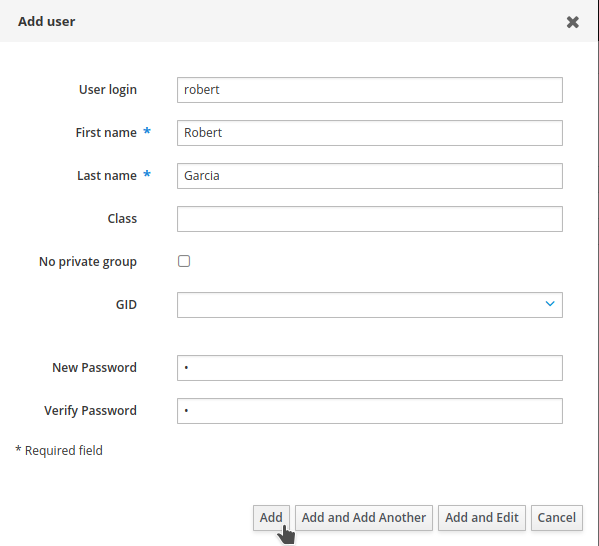
Fill in the user form:
-
User login:
robert -
First name:
Robert -
Last name:
Garcia -
Set a password
-
-
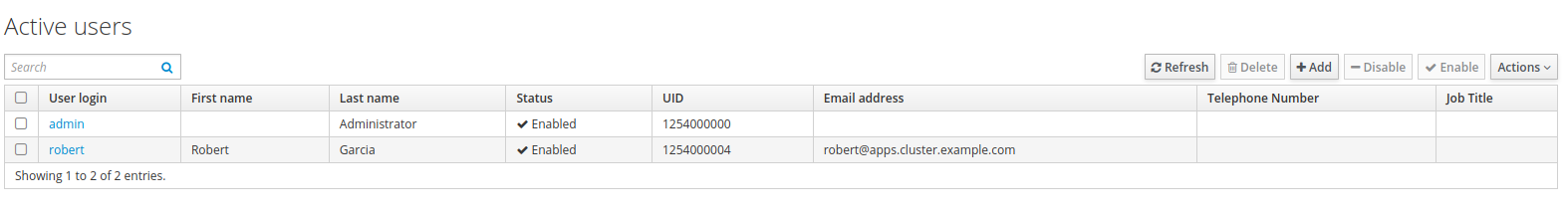
Click
Add.
Creating a group in FreeIPA
-
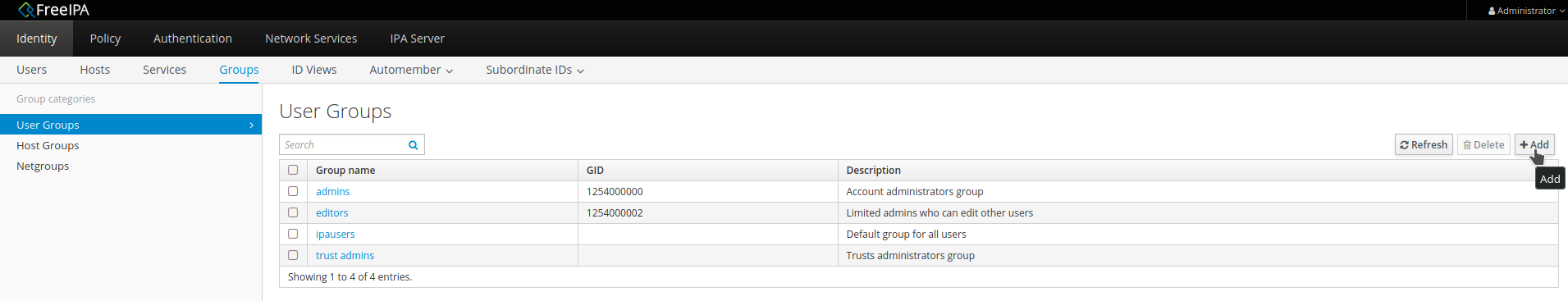
Go to
Identity→Groups. ClickAdd.
-
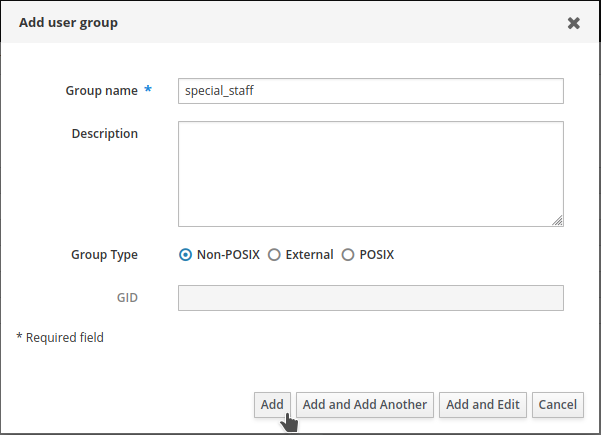
Add a
Non-POSIXgroup namedspecial_staff. ClickAdd.
-
Assign
robertto thespecial_staffgroup: -
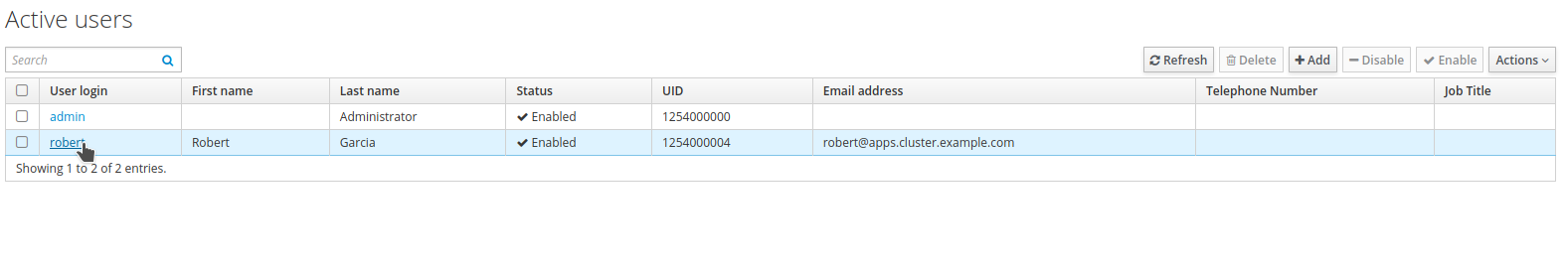
Browse to
Identity→Users. Select the userrobert.
-
Click the
User Groupstab, thenAdd.
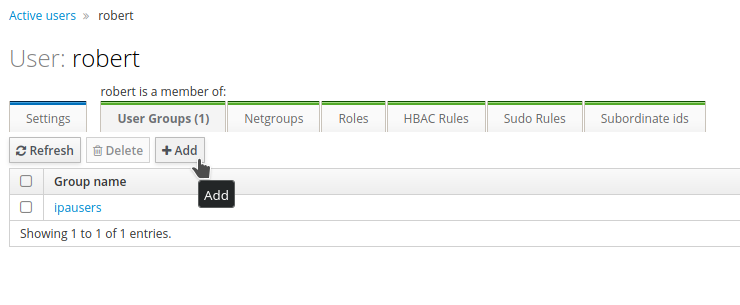
-
Select
special_staffand clickAdd.
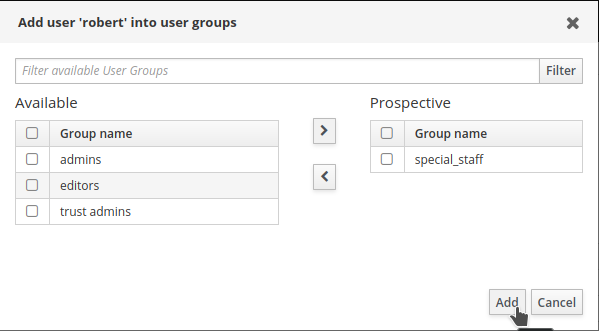
Configuring LDAP in RH-SSO
-
Open the RH-SSO administration web console.
-
Select the
Demorealm. -
Click
User Federation.
-
Select
ldapas the provider.
-
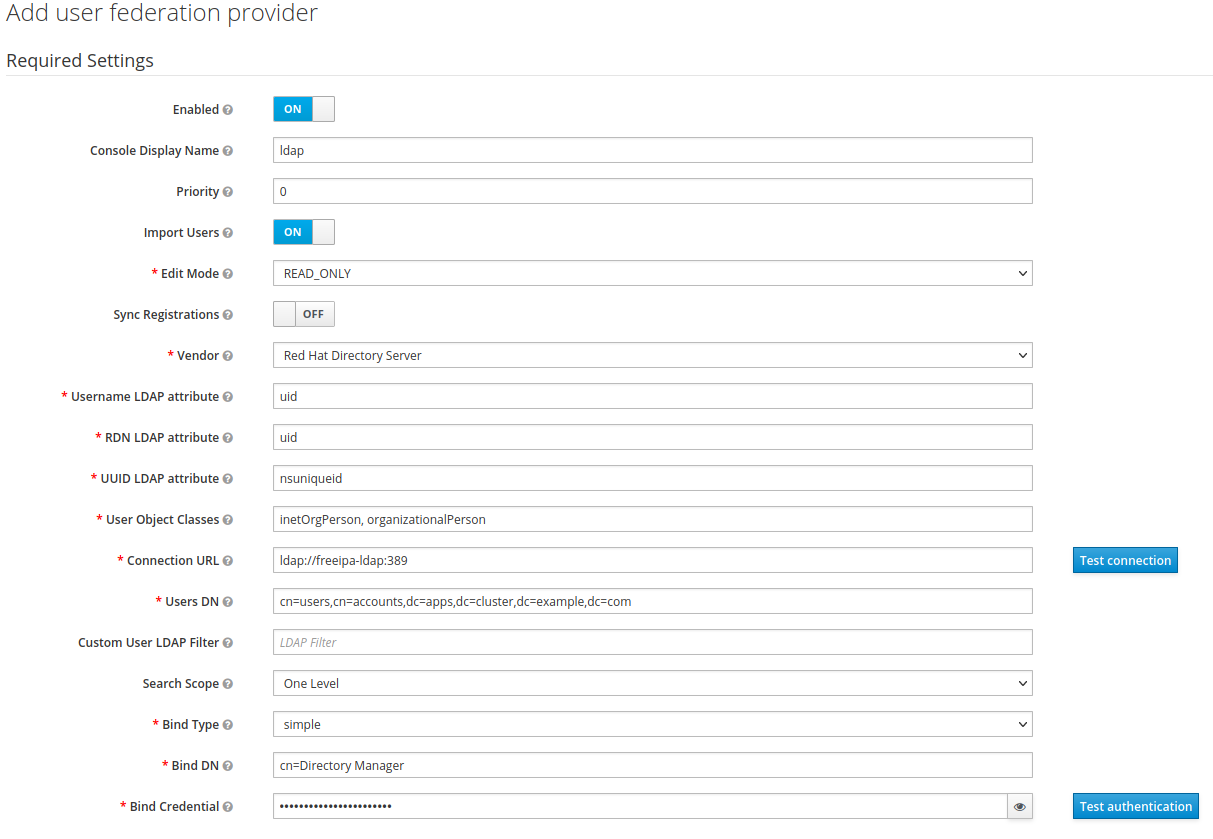
Fill in the required settings for the LDAP provider and click
Save.
-
Click
Synchronize all users.
We are using a plain LDAP connection for this workshop. To use SSL, change the service port to 636 and the protocol to ldaps.
|
The Bind Credential is the password for the Directory Manager account in FreeIPA. This account is created during the FreeIPA installation and has full administrative privileges.
|
Configuring the group mapper
-
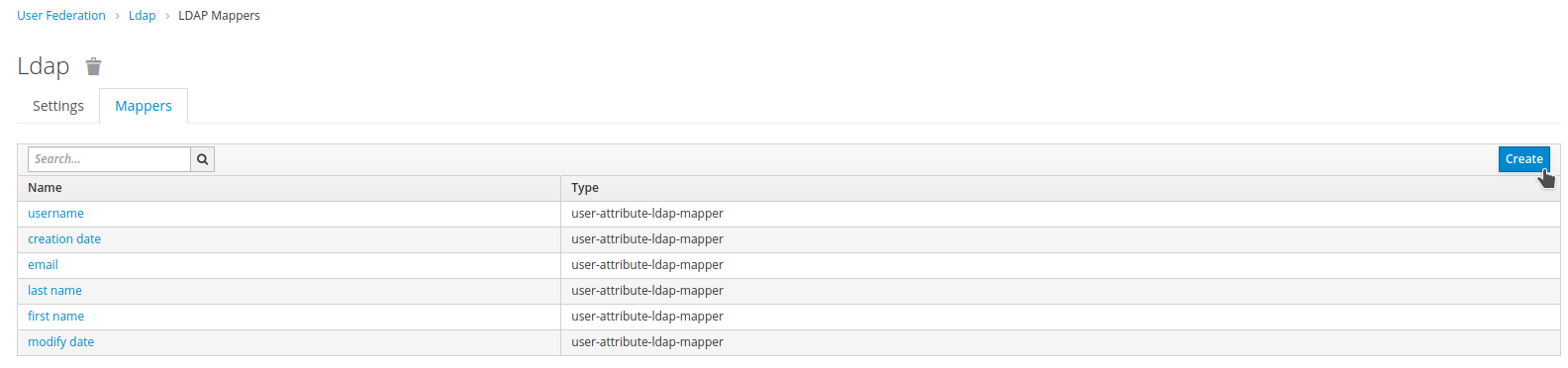
Click the
Mapperstab. ClickCreate.
-
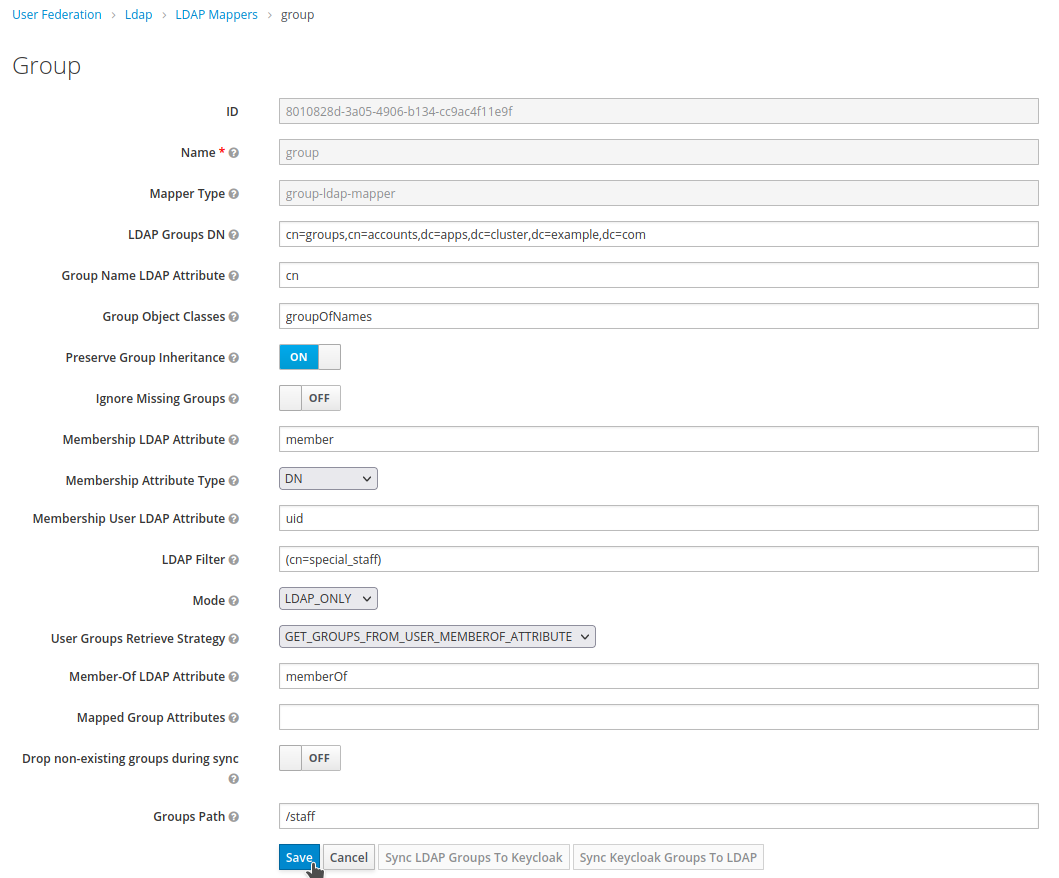
Configure the mapper:
-
Name:
group -
Mapper Type:
group-ldap-mapper -
Fill in the remaining fields and click
Save.
-
-
Click
Sync LDAP Groups To Keycloak. -
Verify that the group has been imported successfully:
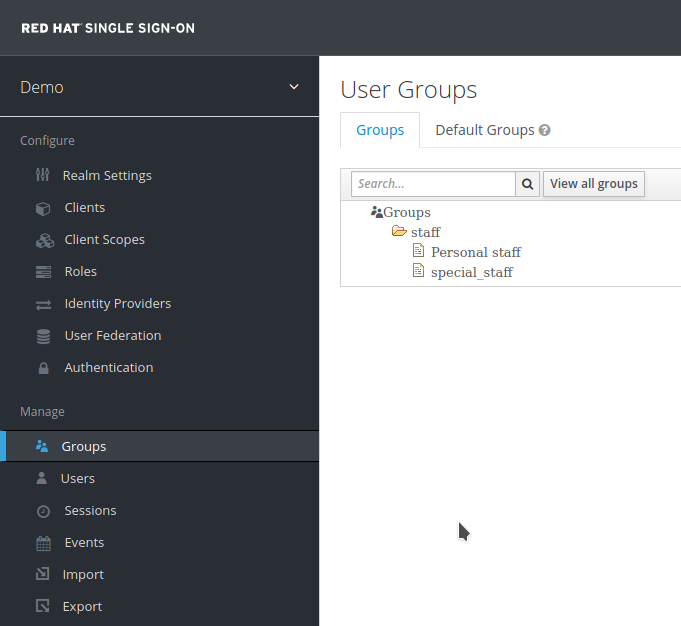
-
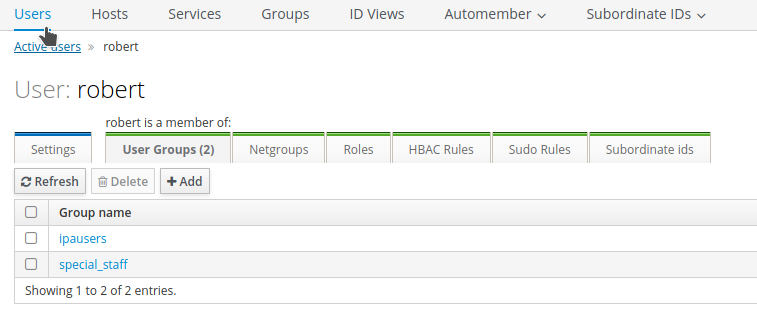
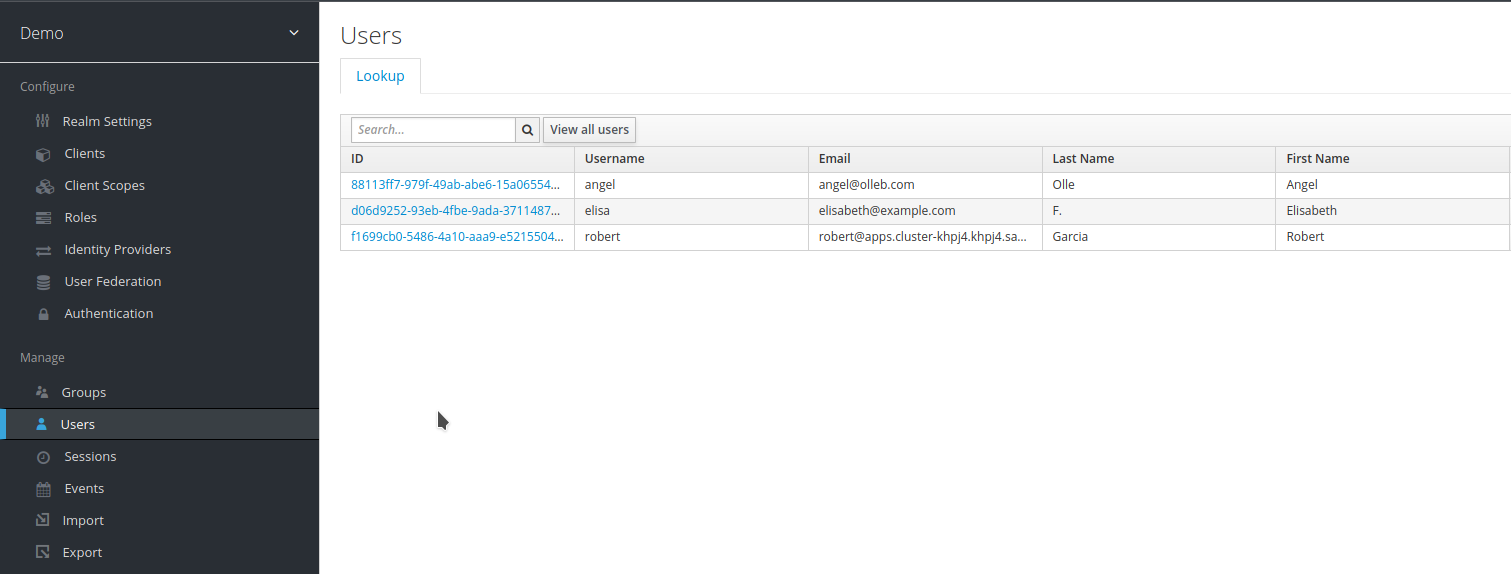
Also, check that the user
roberthas been imported:
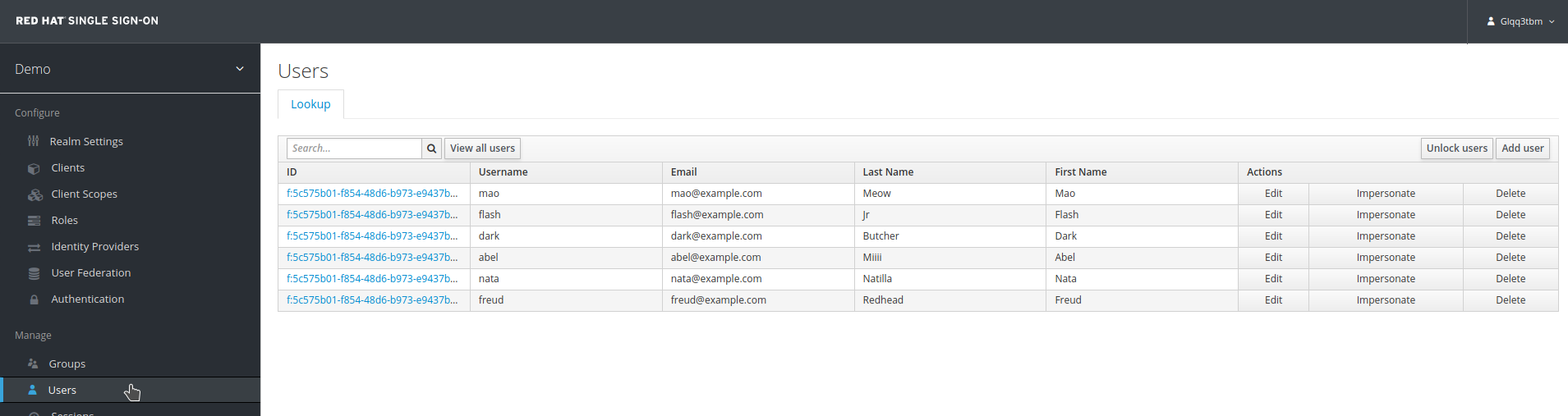
User Storage SPI
External User REST Service Store
We have an external system that stores and manages user data, accessible via a REST API.
However, due to certain constraints, we do not want to migrate this existing system to the Red Hat Single Sign-On (RH-SSO) data model. Instead, we aim to integrate our RH-SSO deployment with this external user storage system.
The REST API is implemented using Quarkus and is named jaxrs-user-store. It provides two endpoints:
-
/api/v1/users– returns all users in the system. -
/api/v1/users/{id}– returns the user matching theuserIdwithid.
Both endpoints accept GET requests.
Deploying the application
The application is designed to run on OpenShift. You can deploy it by executing the ocp-deploy.sh script or, alternatively:
./mvnw install -Dquarkus.kubernetes.deploy=trueTesting the application endpoints
$ http ${APP_HOSTNAME}/api/v1/users
HTTP/1.1 200 OK
Content-Type: application/json
content-length: 731
[
<..>
{
"email": "[email protected]",
"firstName": "Abel",
"lastName": "Miiii",
"password": "abelpassword",
"userId": "5",
"username": "abel"
},
{
"email": "[email protected]",
"firstName": "Mao",
"lastName": "Meow",
"password": "maopassword",
"userId": "3",
"username": "mao"
}
<..>
]$ http localhost:8081/api/v1/users/1
HTTP/1.1 200 OK
Content-Type: application/json
content-length: 120
{
"email": "[email protected]",
"firstName": "Nata",
"lastName": "Natilla",
"password": "natapassword",
"userId": "1",
"username": "nata"
}Extending RH-SSO with the User Storage SPI
To connect RH-SSO to the external system, we use the User Storage SPI (Service Provider Interface).
The provider implementation is called custom-user-storage-spi and can be deployed using several methods:
-
Extending the RH-SSO image.
-
Mounting a volume with the JAR file.
-
Using a ConfigMap (not recommended for large files; better for metadata only).
-
Copying the JAR into the pod (ephemeral storage).
-
Other deployment methods as required.
The provider reads the USER_STORAGE_CUSTOM_SPI_TARGET_HOST environment variable in the following format: HOST:PORT or just HOST (defaults to port 80).
This value can be provided in the DeploymentConfig environment variables.
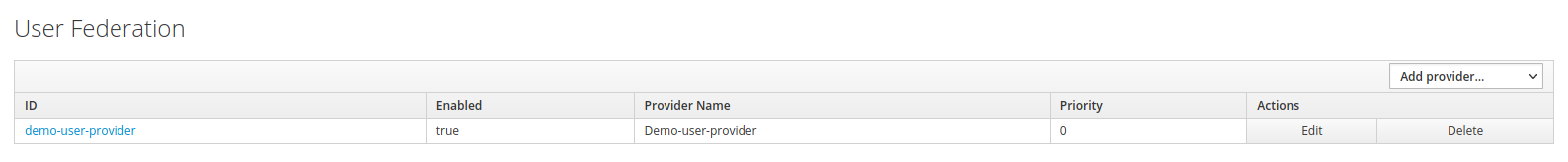
Once the package is deployed and the environment variable is set, the new provider will appear in the RH-SSO admin console under User Federation.
-
Click
demo-user-provider.
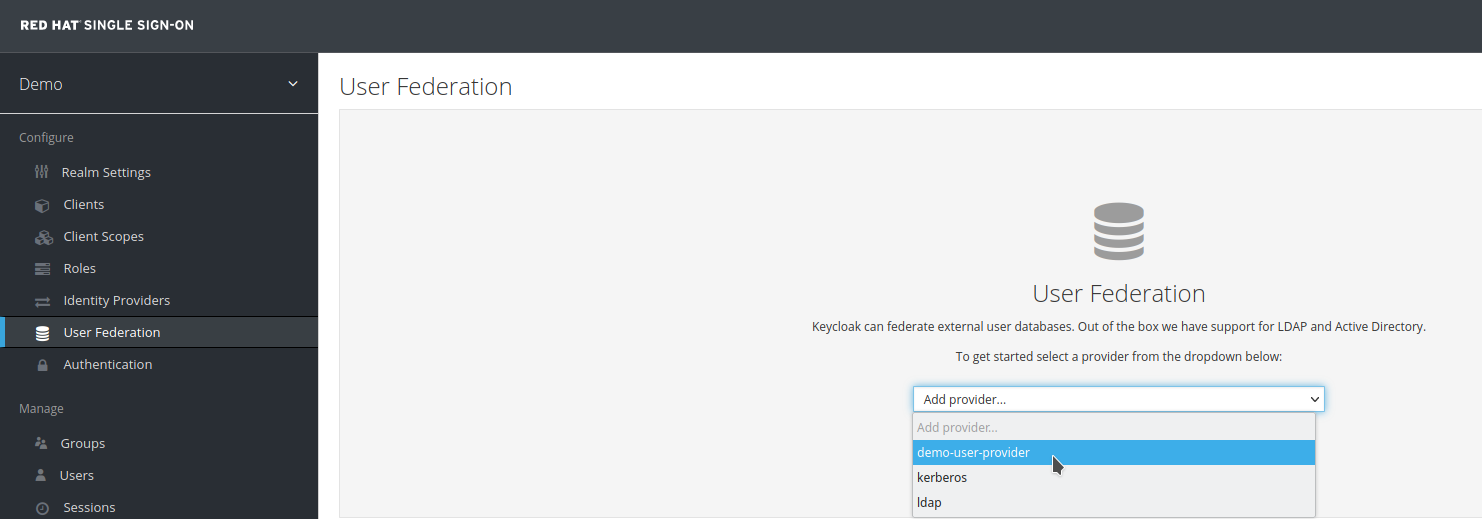
-
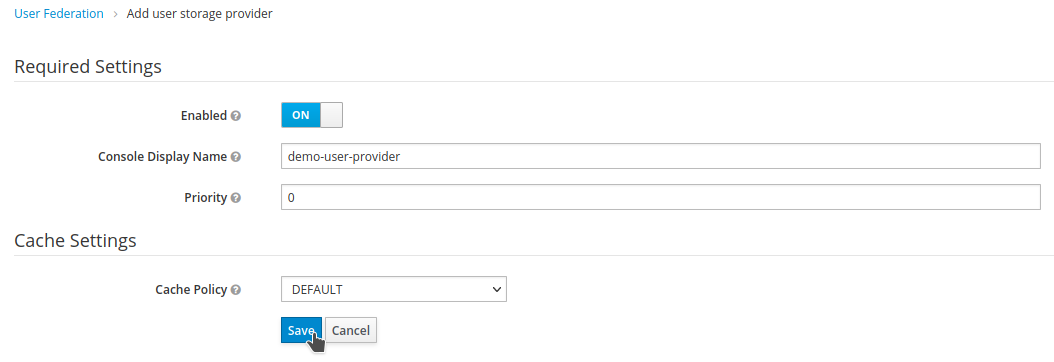
Verify that the provider is
Enabledand clickSave.
-
Click
Users. The external storage users should now be loaded into RH-SSO.