Environment Setup
|
This tutorial was developed and tested with:
|
Workshop Tools
The following tools are required to run the exercises in this tutorial. Please ensure that they are installed and properly configured before proceeding with any of the tutorial chapters.
| Tool | Reference |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
| The extensions source code used during this workshop can be found at the following URL: https://github.com/aolle/rhsso-workshop-code |
Deploying Red Hat Single Sign-On for OpenShift
Red Hat Single Sign-On can be deployed using either the Operator or the application template.
The Operator automates and simplifies the administration tasks in Red Hat OpenShift using custom resources (CRs). It means that we can create Red Hat Single Sign-On resources using these custom resources instead of using the Red Hat Single Sign-On admin console.
The Operator performs a one-way synchronization of the CRs. If we modify a CR directly (for example, using oc) the changes show up in the Red Hat Single Sign-On admin console. However, if the same resource is modified using the admin console, those changes have no effect on the CR.
|
If the Red Hat Single Sign-On fails during deployment, check if a LimitRange exists in the current Red Hat OpenShift project. Sometimes, the RHPDS environment automatically creates a LimitRange when a new project is created. Also, check the health check probes. The initial delay may require a higher value.
|
| For this workshop, we assume that Red Hat Single Sign-On has been installed using the templates and imagestream method explained in 1.2.2 Deploying Red Hat Single Sign-On for Red Hat OpenShift using the templates. Additionally, for convenience and simplification purposes, we will depoy applications and services in the same project where Red Hat Single Sign-On is deployed. |
Deploying Red Hat Single Sign-On for OpenShift using the Operator
You can use the Red Hat OpenShift Container Platform web console to subscribe and deploy the Red Hat Single Sign-on Operator. The Red Hat Single Sign-On Operator simplifies the deployment process and it is ease to use, but less flexible than the template-based deployment.
Check the supported CRs here:
-
Open a browser window and log in to the Red Hat OpenShift Container Platform web console.
-
From the Administrator perspective, click
Operators, thenOperatorHub. -
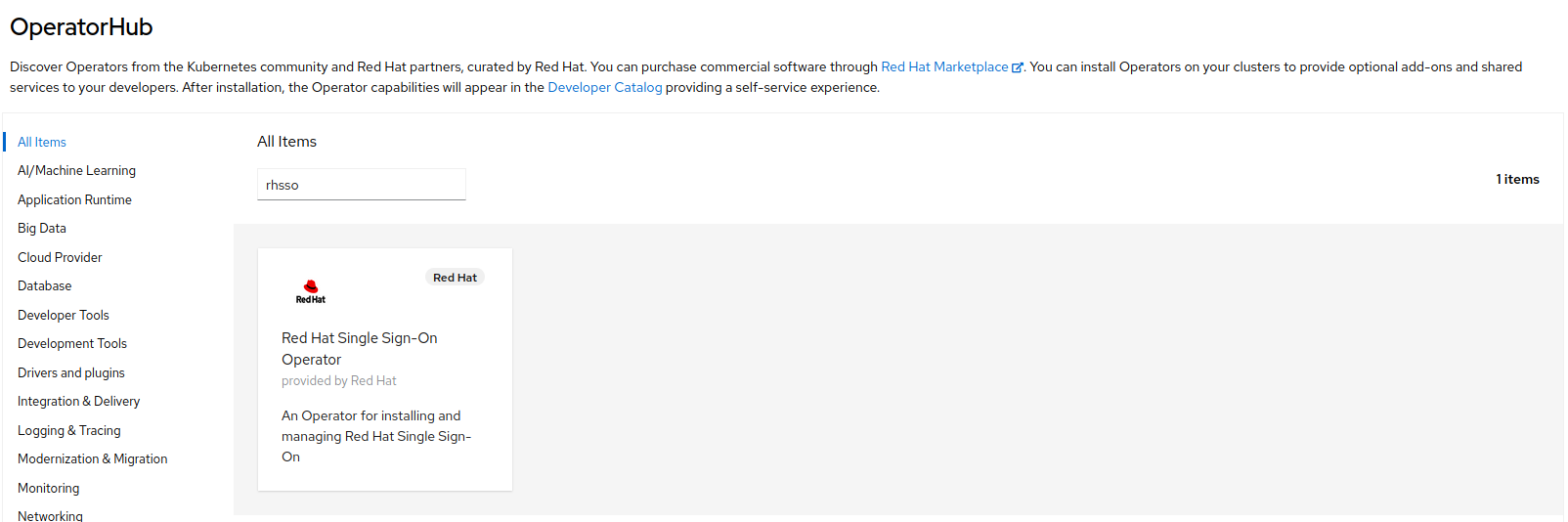
In the Filter by keyword field, type
rhsso.
-
Select the Red Hat Single Sign-On Operator tile and click
Install.
-
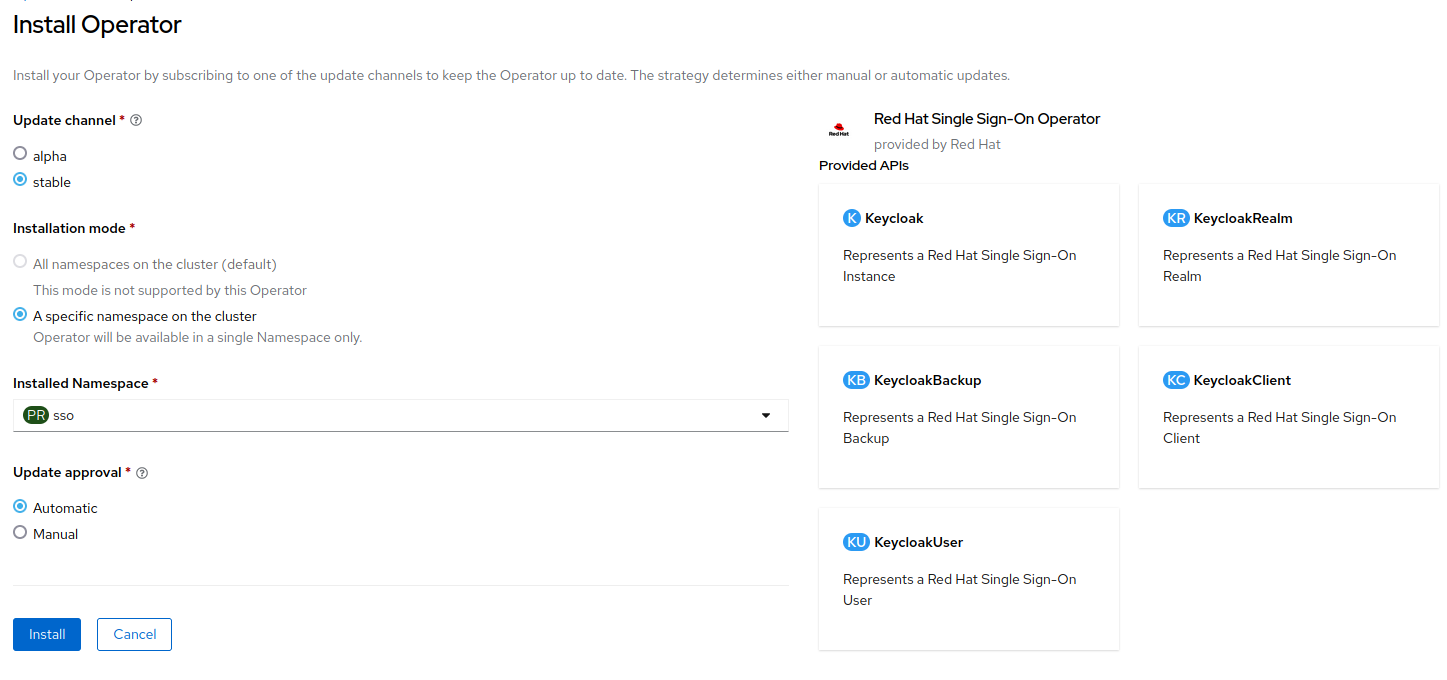
On the Install Operator page, leave
stablefrom the list of availableUpdate Channeloptions. The Operator supports only theA specific namespace on the clusteras installation mode. Create thessoproject. ChooseAutomaticupdate approval.
-
Click
Install.
Installing Red Hat Single Sign-On using a custom resource:
-
From the Administrator perspective, click on
Operators, then selectInstalled Operators. Make sure to selectssoproject. Select Red Hat Single Sign-On Operator. -
Click
Create instanceof the Keycloak tile.
-
Change the
Nameif desired. Then, clickCreate.
Deploying Red Hat Single Sign-On for OpenShift using the templates
-
Create the templates and install the Red Hat Single Sign-On image stream.
For this workshop, we will use the sso76-ocp4-x509-postgresql-persistent template, which is Red Hat Single Sign-On 7.6 on OpenJDK + PostgreSQL (Persistent) for Red Hat OpenShift 4.X. The template does not require the manual creation of the keystores or truststores.
|
oc replace -n openshift --force -f \
https://raw.githubusercontent.com/jboss-container-images/redhat-sso-7-openshift-image/sso76-dev/templates/sso76-image-stream.json
oc replace -n openshift --force -f \
https://raw.githubusercontent.com/jboss-container-images/redhat-sso-7-openshift-image/sso76-dev/templates/reencrypt/ocp-4.x/sso76-ocp4-x509-postgresql-persistent.json
oc -n openshift import-image rh-sso-7/sso76-openshift-rhel8:7.6 --from=registry.redhat.io/rh-sso-7/sso76-openshift-rhel8:7.6 --confirm-
Create the new project.
oc new-project sso-
Add the
viewrole to thedefaultservice account.
oc policy add-role-to-user view -z default -n sso-
Deploy the template.
oc new-app --template=sso76-ocp4-x509-postgresql-persistent
Write down the auto-generated RH-SSO Administrator Username and RH-SSO Administrator Password required for login in to the Red Hat Single Sign-On admin console.
|
1.3 Deploying an Identity Management (IdM/FreeIPA) on Red Hat OpenShift
This section explains how to install FreeIPA, an Identity Management (IdM) solution that combines Linux, 389 Directory Server, MIT Kerberos, NTP, DNS and Dogtag.
FreeIPA is the upstream version of Red Hat Identity Management.
Later on, we will see how we can integrate Red Hat Single Sign-On with IdM/FreeIPA.
To get started, stay logged in into your Red Hat OpenShift platform, and for convenience, select the sso project that has been created previously. Follow the steps below for deploying a FreeIPA instance on top of Red Hat OpenShift.
# export the image that we are going to deploy
export IMG=quay.io/freeipa/freeipa-openshift-container:latest
export IMG_BASE=${IMG}
# clone the repository and deploy the roles and scc
# if preferred, a remote build could be performed instead of cloning the repository
git clone https://github.com/freeipa/freeipa-openshift-container.git
cd freeipa-openshift-container/
kustomize build deploy/admin | oc create -f -
# create the ocp template and deploy it
make template-create
make template-new-appWrite down the IPA_ADMIN_PASSWORD and IPA_DM_PASSWORD displayed on the terminal; we will need it later.
Open the FreeIPA administration console to verify that the access and credentials are working properly.