Securing web applications and services with Red Hat Single Sign-On
Configuring the Realm, roles, groups and users
Before proceeding with the next sections, we need to configure the realm, roles and users in our Red Hat Single Sign-On instance.
-
Open a browser window and log in to the Red Hat Single Sign-On administration web console.
-
Create the
demorealm. Click on theAdd realmbutton, provide the realm name, and clickCreate.

-
Create the
staffgroup. Click onGroups.
-
Then click
New.
-
Set
staffas the group name, and clickSave.

-
Create the subgroup named
Personal staff. Click onGroups, select thestaffgroup, and clickNew.
-
Set
Personal staffas the name, and clickSave.
-
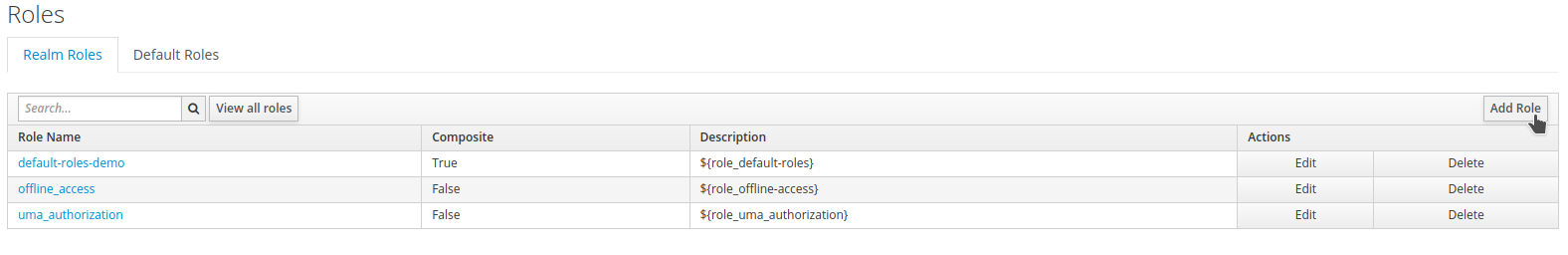
Create the role
vet. Click onRoles, thenAdd Role.
-
Set the Role name, and click
Save.
-
Repeat the same steps for creating a role named
assistant. -
Create the user
angel. Click onUsers, thenAdd user.
-
Set the username, and click
Save.
-
Open the
Credentialstab and set the password for the user. Make sure to setTemporarytoOFFbefore setting the password.
-
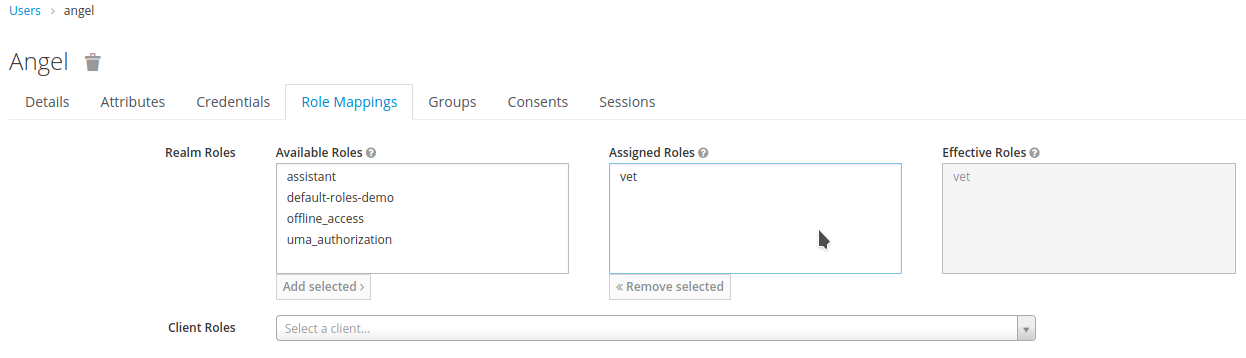
Open the
Role Mappingstab and assign thevetrole to the user.
-
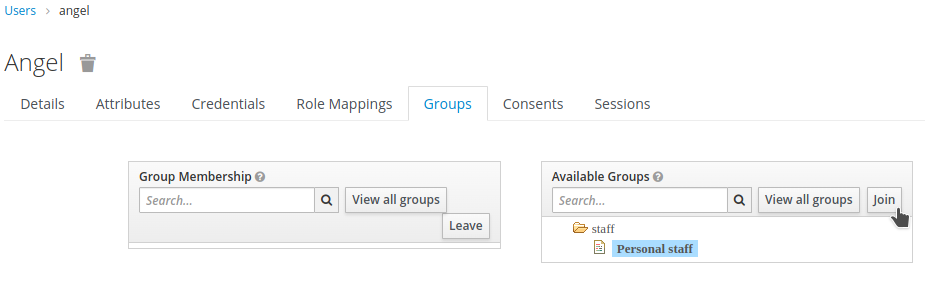
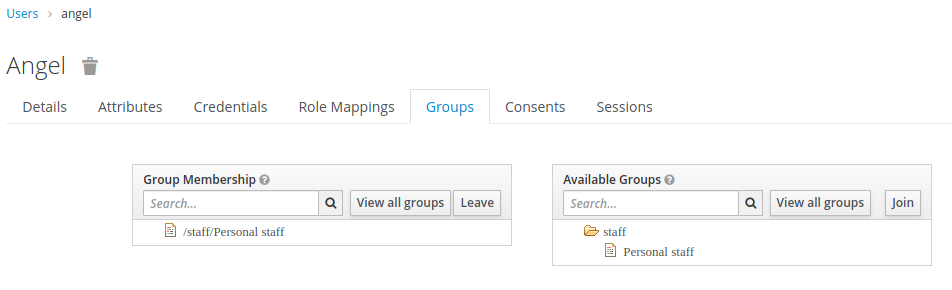
Open the
Groupstab and assign the userangelto thePersonal staffgroup by clicking the group and theJoinbutton.
-
Repeat the same steps for creating a user named
elisabethbut assign theassistantrole. Also, remember to incude the user in thePersonal staffgroup.
Red Hat Single Sign-On allows defining one or more groups as default groups, where any new user will automatically join the defined groups, making it easier to assign users to the same group without repetitive and time-consuming tasks. The option is available by clicking on Groups, then Default Groups.
|
Securing Quarkus web applications using OpenID Connect (OIDC)
The sample application that we will use in this section is the Quarkus Petclinic project.
In this tutorial, we will work with a version that has been modified for the tutorial.
The repository for this modified version is:
To get started, clone the repository and switch to the rh-sso-base-7.6 branch:
git clone -b rh-sso-base-7.6 https://github.com/aolle/quarkus-petclinic.gitThe application is prepared to be deployed on top of Red Hat OpenShift. The application project contains the Quarkus OpenShift extension (k8s with s2i) to automatically generate the OpenShift resources and deploy it.
Test the application, follow these steps:
-
Log into your Red Hat OpenShift cluster.
-
Switch to the
ssoproject if you are not currently using it. -
Deploy the application by executing the
ocp-deploy.shscript or alternatively:
./mvnw install -Dquarkus.kubernetes.deploy=true
During the build, you may encounter the SSLHandshakeException/ValidatorException exception due to self-signed certificate. To solve this, add -Dquarkus.kubernetes-client.trust-certs=true during the build process.
|
-
Open a browser window and visit the application URL.
| Make a note of the application URL as it will be required during the security configuration process. |
Before securing the application, let’s configure a new client in our Red Hat Single Sign-On realm.
-
Open a browser window and log in to the Red Hat Single Sign-On administration web console.
-
Select our
demorealm and clickClients. ClickCreate.
-
Set
quarkus-petclinicasClient ID. ClickSave.

-
On the
quarkus-petclinicclient configuration page:-
Change the
Access Typefrompublictoconfidential. -
Set
Authorization EnabledtoON. -
Set
Valid Redirect URIsto include the root context of your application. For example, if your petclinic application is available athttp://domain.example.com/, writehttp://domain.example.com/*. -
Click
Save.
-
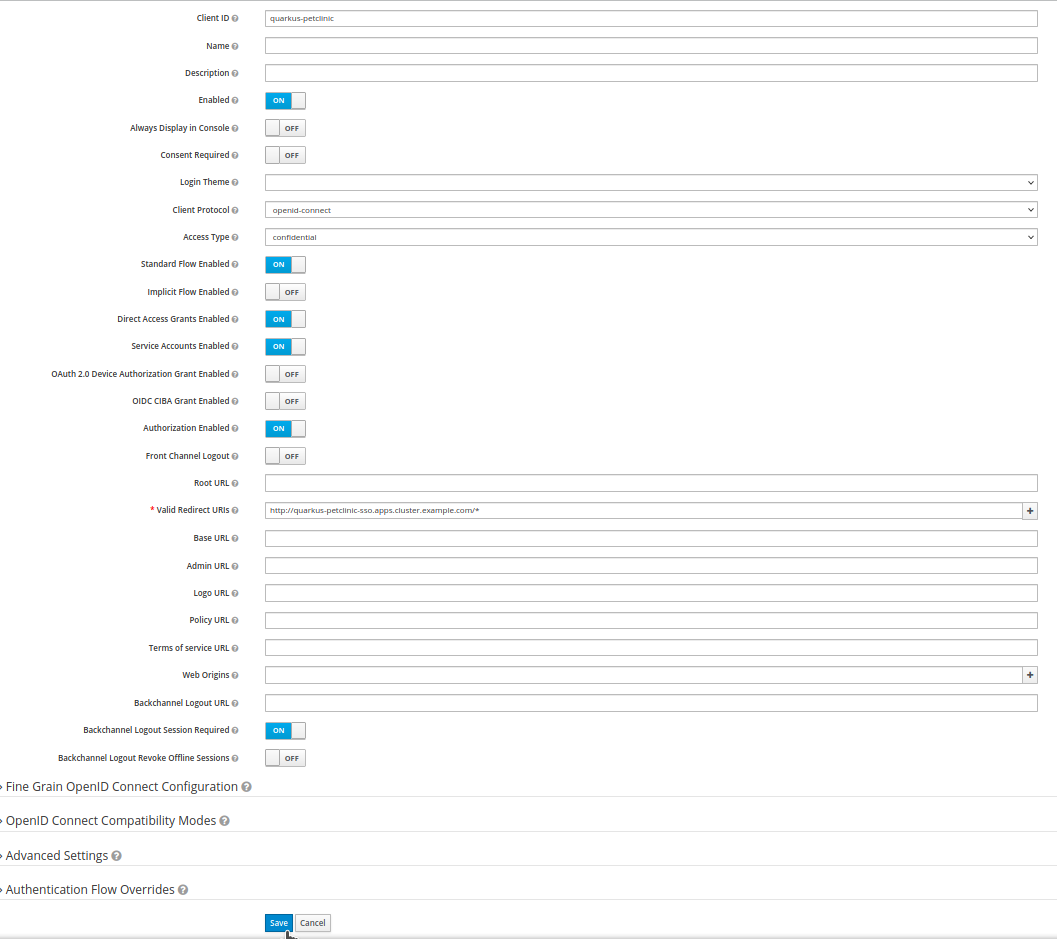
At this point, we have the demo realm with the quarkus-petclinic client; additionally, we created two roles and two users: the user angel that has the vet role and the user elisabeth that has the role assistant.
-
The authorization granularity that we want to configure based on our application is the following:
-
Any user that belongs to the
demorealm, likeelisabeth, can browse the application except theVETERINARIANSresource. -
Only the users with the role
vetcan view theVETERINARIANSresource (which has the/vets.htmlcontext). -
Any other user access outside the realm will be rejected.
-
Let’s configure our client authorization.
-
Open a browser window and log in to the Red Hat Single Sign-On administration web console. Browse to our
quarkus-petclinicclient and click theAuthorizationand thenResourcestabs.
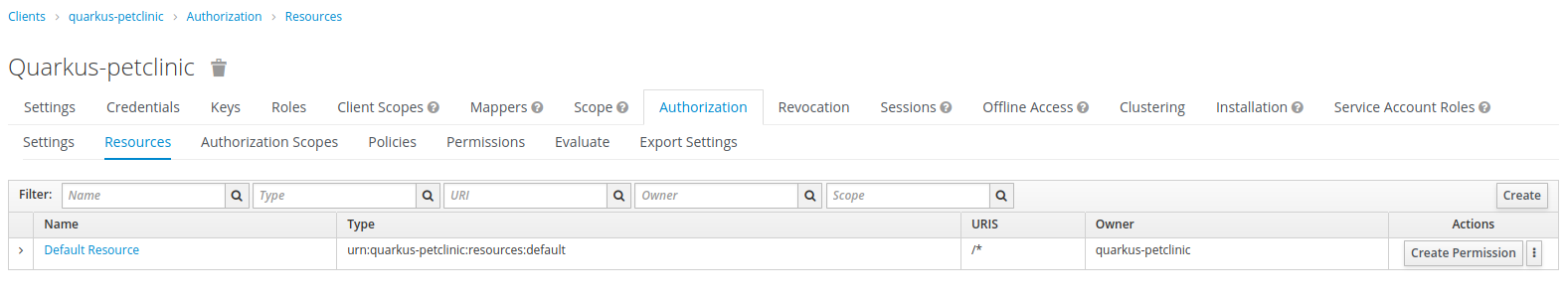
-
Click
Create Permissionfor theDefault Resource.
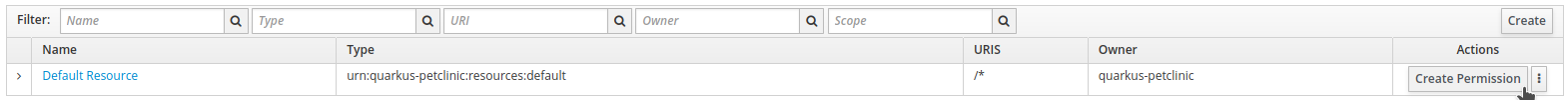
-
Click on
Create Policy…and selectGroup.
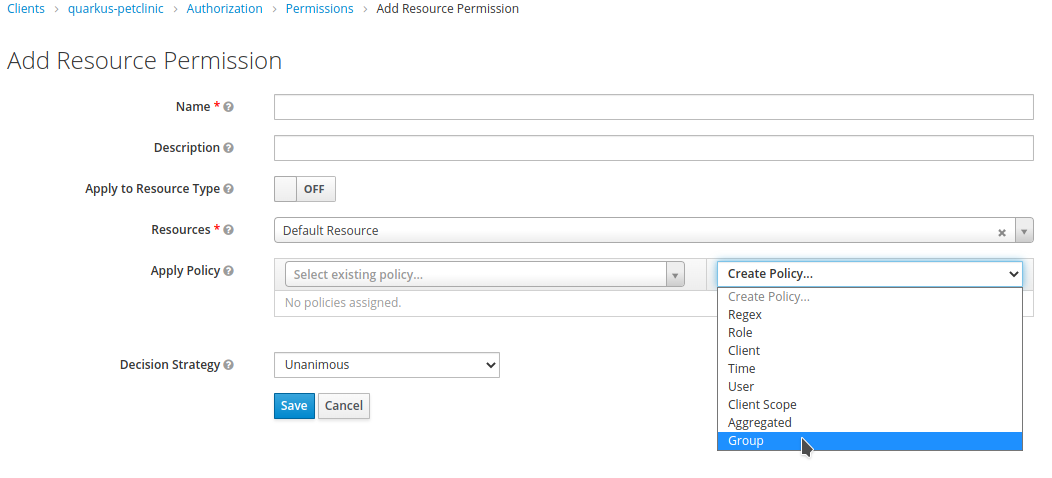
-
Set
Default Group Policyas theName. Selectstafffrom theGroupslist and clickSelect. Make sure that theLogicis set toPositiveandExtend to Childrenis checked (we will use this logic in later chapters). Finally, clickSave.
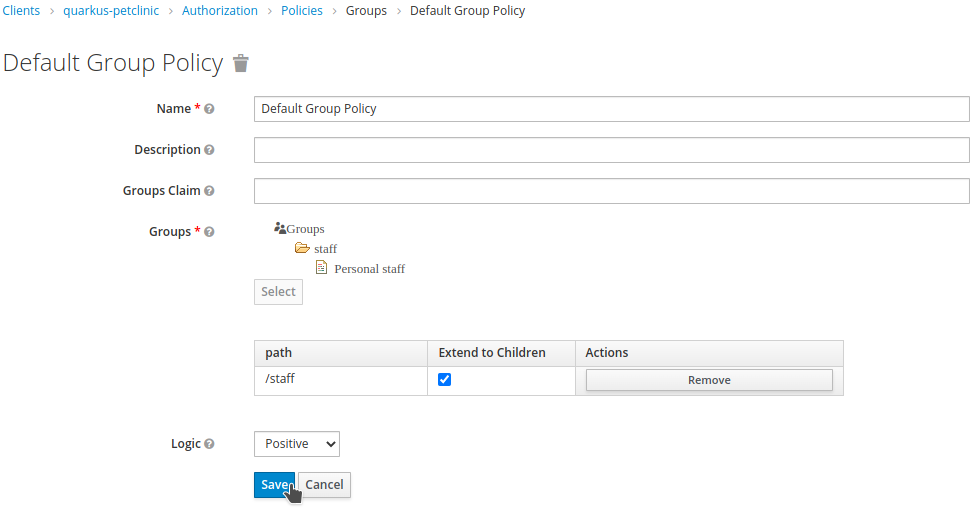
-
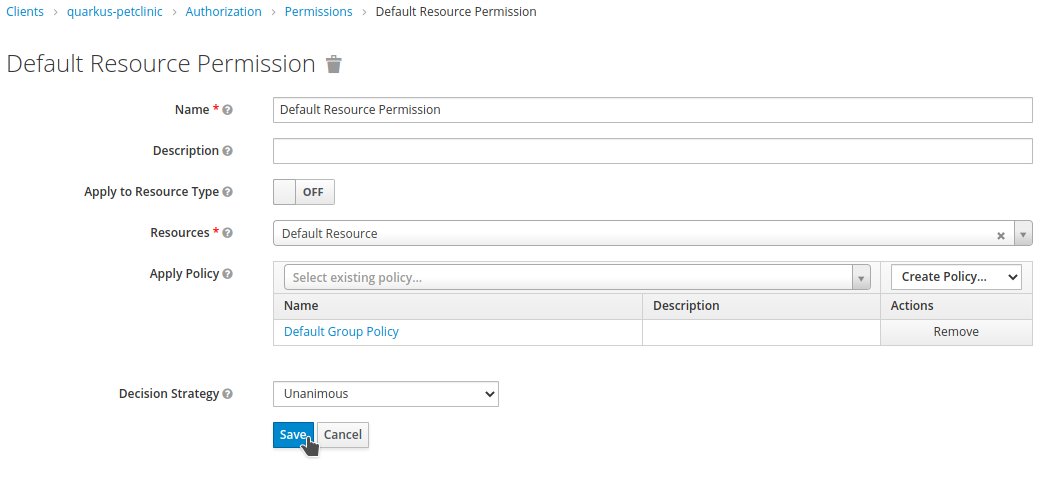
You will be redirected back to the
Add Resource Permissionpage. SetDefault Resource PermissionasNameand selectDefault ResourceasResources. The recently created policy should have been added automatically. ClickSave.
-
Create a new resource by clicking on
Create.
-
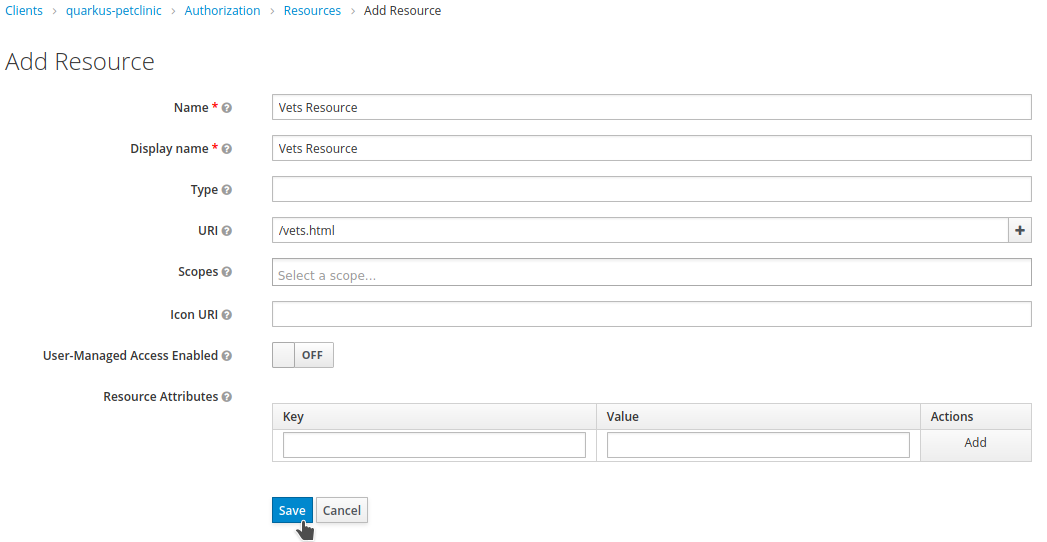
Set
Vets ResourceasNameandDisplay name, and/vets.htmlas URI. ClickSave.
-
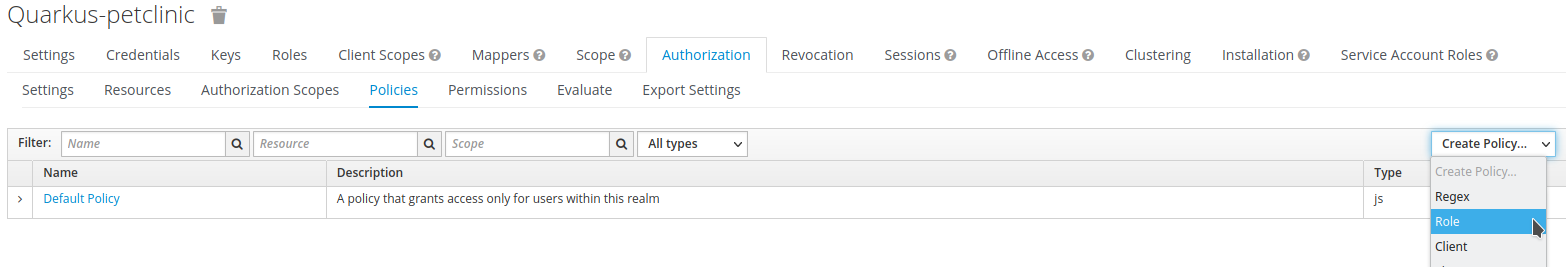
Browse to
AuthorizationandPoliciestabs. Click onCreate Policy…and selectRole.
-
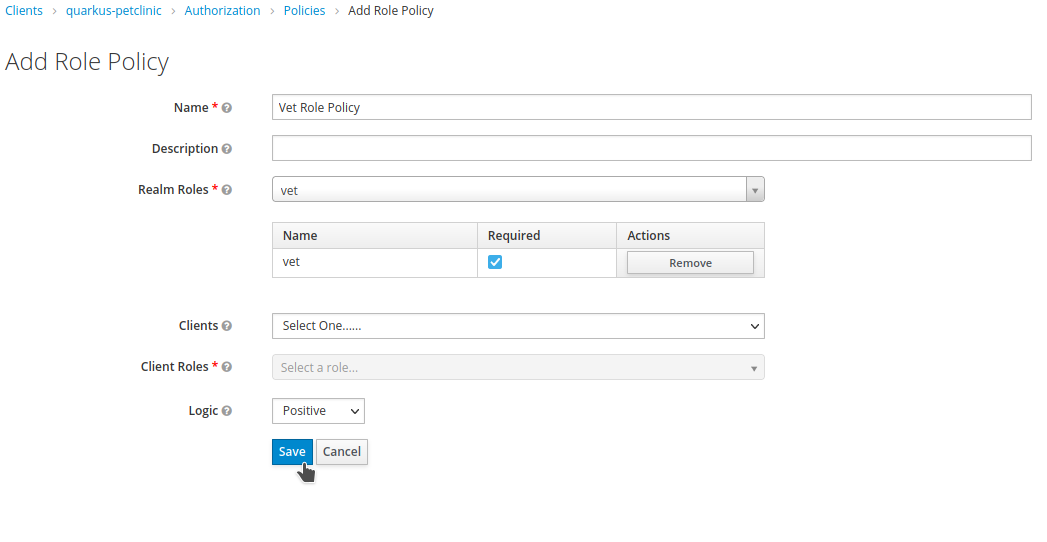
Set
Vet Role Policyas the Name,vetasRealm Roles, and check required. ClickSave.
-
Browse to the
AuthorizationandResourcestabs. -
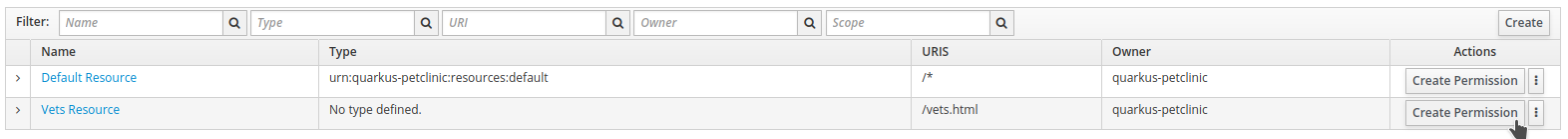
Click on
Create Permissionfor theVets Resource.
-
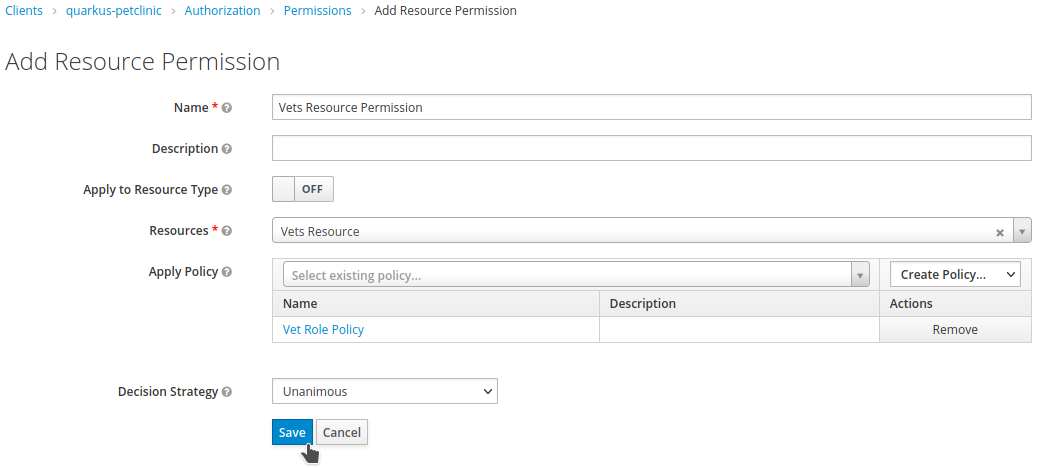
Set
Vets Resource PermissionasName. And apply theVet Role Policy. ClickSave.
At this point, the Red Hat Single Sign-On client is properly configured.
Let’s configure the application side.
-
Open a browser window and log in to the Red Hat Single Sign-On administration web console. Browse to our
quarkus-petclinicclient and click theCredentialstab. Write down theSecretvalue, we will need it soon.
-
Create the ConfigMap with the
SSO_HOSTenvironment variable. Replace{YOUR_SSO_HOST}with the correct value.
oc create configmap quarkus-petclinic-config --from-literal=SSO_HOST={YOUR_SSO_HOST} -n sso-
Create the secret with the OIDC client credentials. Replace the
{YOUR_SSO_CLIENT_SECRET}with the correct value.
oc create secret generic quarkus-petclinic-secret --from-literal=SSO_CLIENT_SECRET={YOUR_SSO_CLIENT_SECRET} -n sso-
Add the following configuration in
application.propertiesas shown:
quarkus.openshift.env.secrets=quarkus-petclinic-secret
quarkus.openshift.env.configmaps=quarkus-petclinic-config
quarkus.oidc.auth-server-url=https://${SSO_HOST:localhost:8080}/auth/realms/demo
quarkus.oidc.client-id=quarkus-petclinic
quarkus.oidc.credentials.secret=${SSO_CLIENT_SECRET:secret}
quarkus.oidc.tls.verification=none
quarkus.oidc.roles.source=accesstoken
quarkus.oidc.application-type=web-app
quarkus.oidc.webapp.auth-server-url=${quarkus.oidc.auth-server-url}
quarkus.oidc.webapp.client-id=${quarkus.oidc.client-id}
quarkus.oidc.webapp.credentials.secret=${quarkus.oidc.credentials.secret}
quarkus.oidc.webapp.roles.source=${quarkus.oidc.roles.source}
quarkus.keycloak.policy-enforcer.enable=true-
Redeploy and test the application accesses:
-
Open a new incognito browser session.
-
Browse to the context root of the Quarkus Petclinic application. The request will be redirected to the Red Hat Single Sign-On login page. Here, we checked that the anonymous access to the application is forbidden.
-
Log in as
elisabeth. The request will be redirected to the application after a successful login. -
Browse through the application, try to access the VETERINARIANS section. The access should be denied, as
elisabethhas theassistantrole and the access is restricted to thevetrole. An error will be shown on the application page. -
Close the browser and open a new one incognito session.
-
Visit the context root of the application again.
-
Login as
angel. -
Browse through the application, try to access the VETERINARIANS section. The access should be granted, as
angelhas thevetrole.
-
A complete OIDC working Petclinic Quarkus application is available at rh-sso-oidc-7.6 branch.
|