Authorization Services
Configuration
Before proceeding with the next sections, we need to configure the realm, roles, and users in our Red Hat build of Keycloak instance.
-
Open a browser window and log in to the Red Hat build of Keycloak administration console.
-
Create the
demorealm. Click themasterrealm dropdown menu and selectCreate Realm.
-
Click
Create.
-
Create the
staffgroup. Click onGroups.
-
Then click
Create group.
-
Set
staffas the group name and clickCreate.
-
Create the child group named
Personal staff. Click on the kebab menu (⋮) of thestaffgroup and selectCreate child group.
-
Set
Personal staffas the name and clickCreate.
-
Create the
vetrole. Click onRealm roles, thenCreate role.
-
Set the role name and click
Save.
-
Repeat the same steps to create a role named
assistant.
-
Create the user
angel. Click onUsers, thenAdd user.
-
Set the username and click
Create.
-
Open the
Credentialstab and set a password for the user. Ensure thatTemporaryis set toOFFbefore setting the password.
-
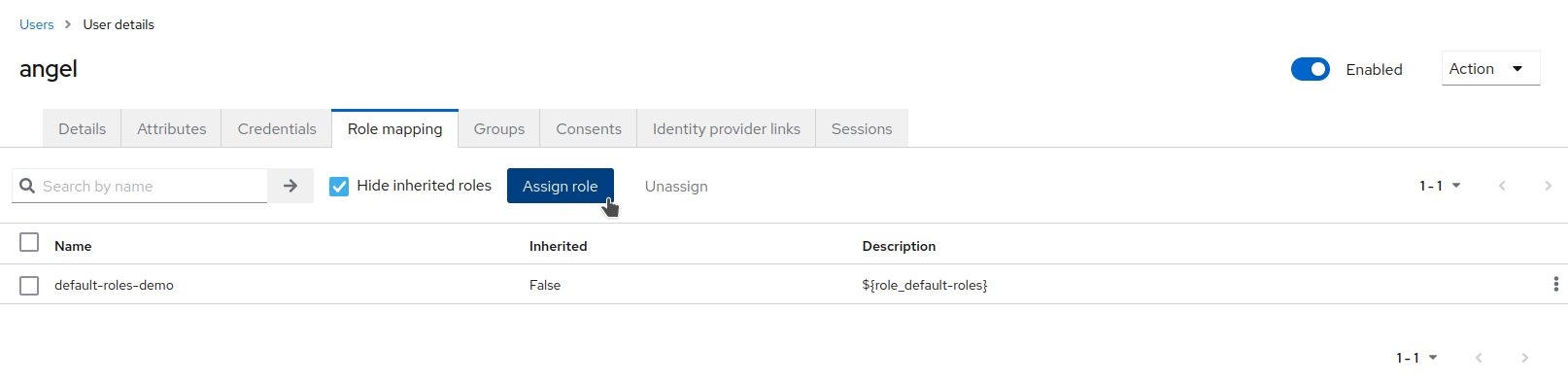
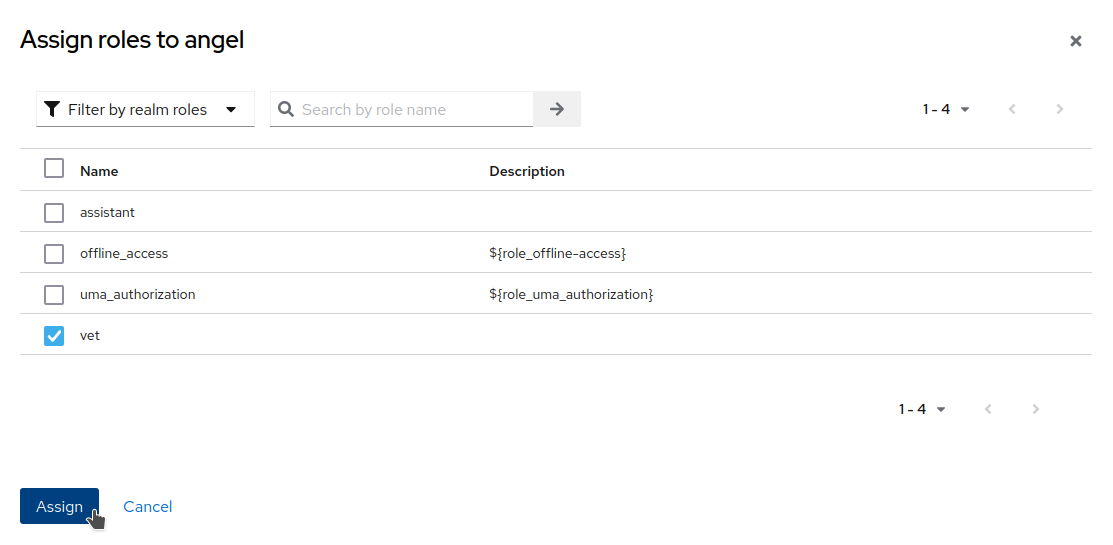
Open the
Role Mappingstab and assign thevetrole to the user.
-
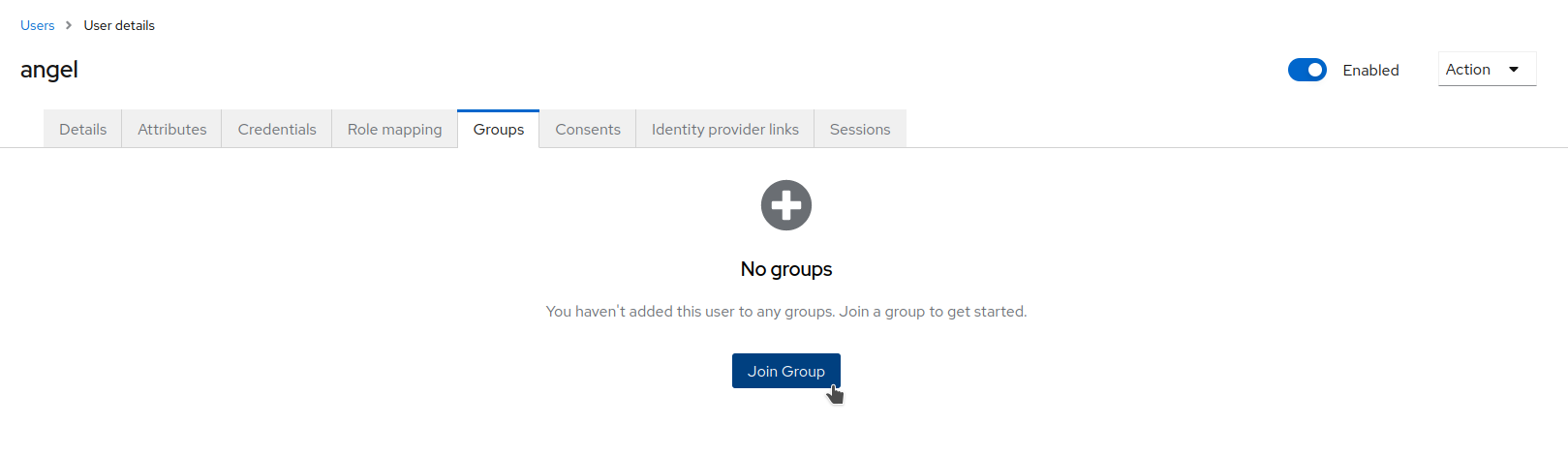
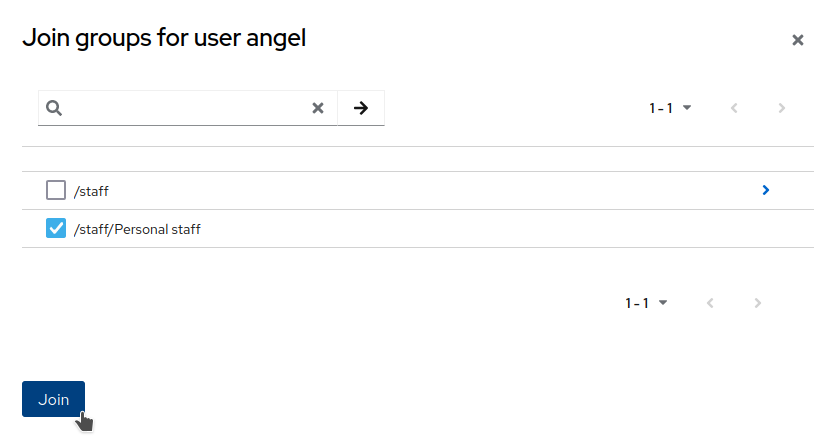
Open the
Groupstab and assign the userangelto thePersonal staffgroup.
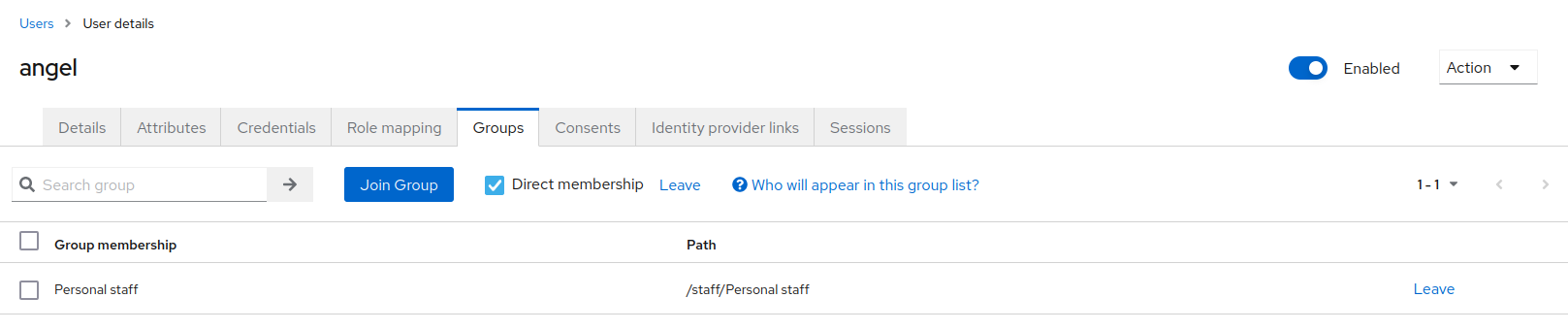
-
Repeat the same steps to create a user named
elisabeth, assigning theassistantrole and adding the user to thePersonal staffgroup.
Securing Web Applications
The sample application used in this section is the Quarkus Petclinic project.
In this tutorial, we will work with a version that has been modified for demonstration purposes.
The repository for this modified version is:
To get started, clone the repository and switch to the rhbk-base-22 branch:
git clone -b rhbk-base-22 https://github.com/atarazana/quarkus-petclinic.gitTest the application:
./mvnw clean quarkus:dev-
Open a browser window and visit the application URL.
Before securing the application, let’s configure a new client in our Red Hat build of Keycloak realm.
-
Open a browser window and log in to the Red Hat build of Keycloak administration console.
-
Select the
demorealm and clickClients. ClickCreate client.
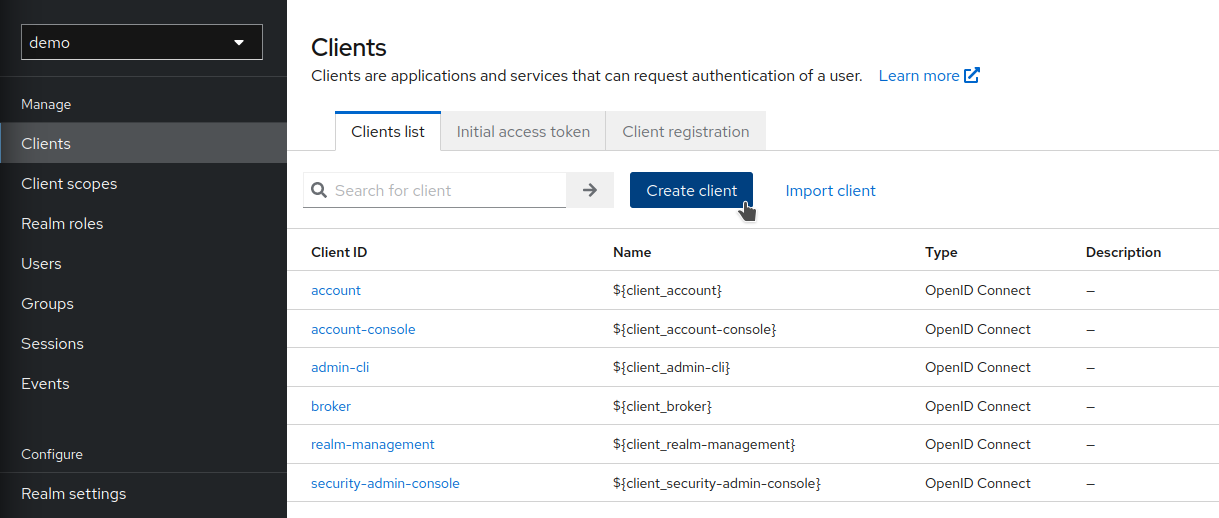
-
Set
quarkus-petclinicas theClient ID. ClickNextuntilSave.
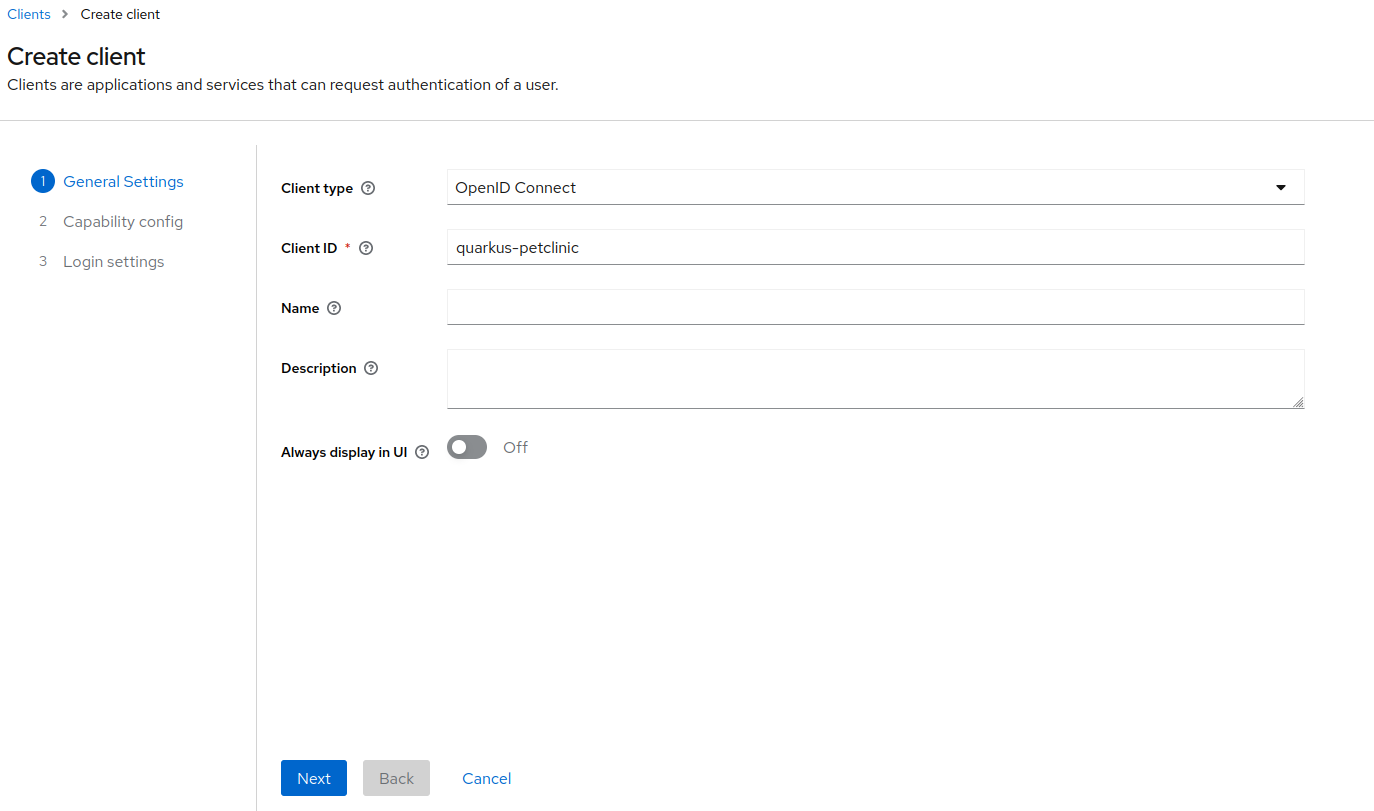
-
On the
quarkus-petclinicclient configuration page:-
Enable
Client authentication. -
Enable
Authorization. -
Set
Valid Redirect URIsto include the root context of your application. -
Click
Save.
-
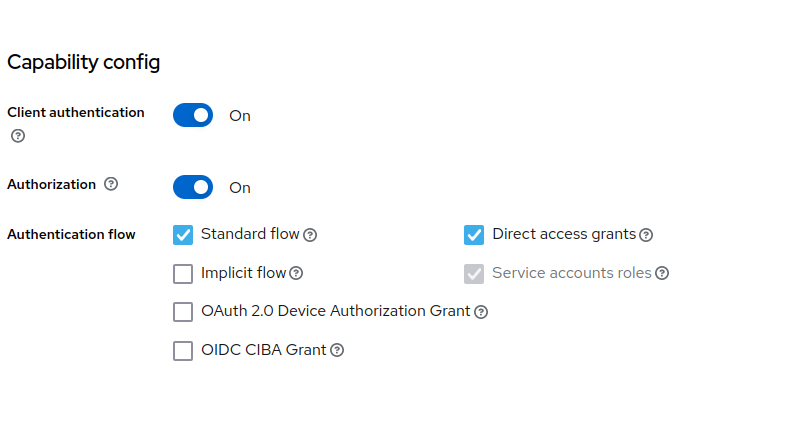
At this point, we have the demo realm with the quarkus-petclinic client. We also created two roles and two users:
the user angel with the vet role, and the user elisabeth with the assistant role.
-
The authorization granularity we want to configure in our application is as follows:
-
Any user that belongs to the
demorealm, likeelisabeth, can browse the application except for theVETERINARIANSresource. -
Only users with the
vetrole can view theVETERINARIANSresource (which corresponds to the/vets.htmlpath). -
Any user outside the realm will be denied access.
-
Let’s configure our client authorization.
-
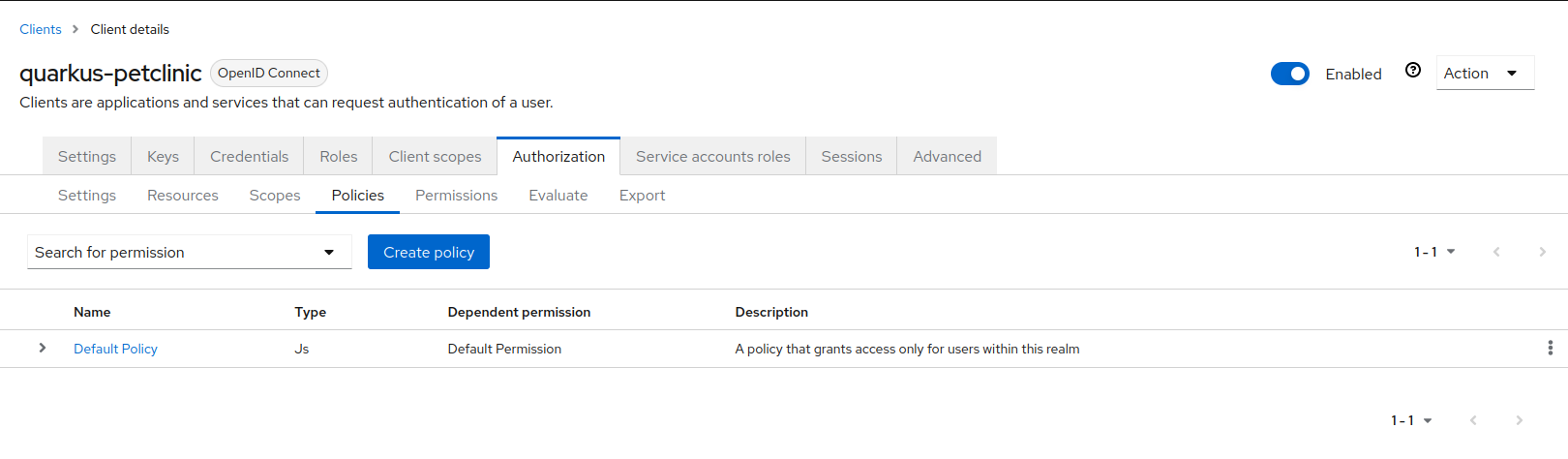
Open a browser window and log in to the Red Hat build of Keycloak administration console. Browse to the
quarkus-petclinicclient and click theAuthorizationtab, then thePoliciestab.
-
Click
Create policyand selectGroup.
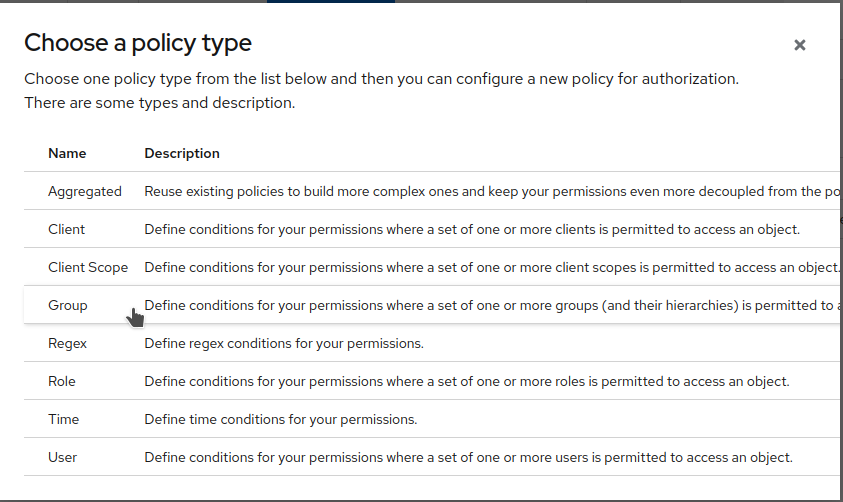
-
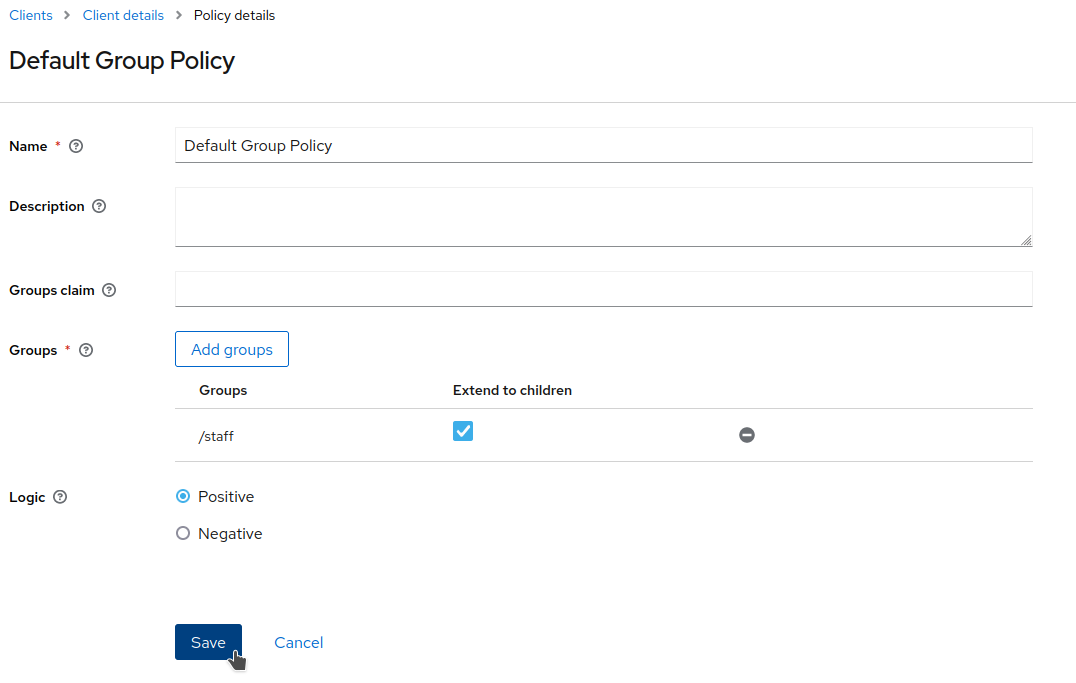
Set
Default Group Policyas theName. Add thestaffgroup to theGroupslist. Ensure that theLogicis set toPositiveand thatExtend to Childrenis checked (to enable it, you may need to clickSavefirst). Finally, clickSave.
-
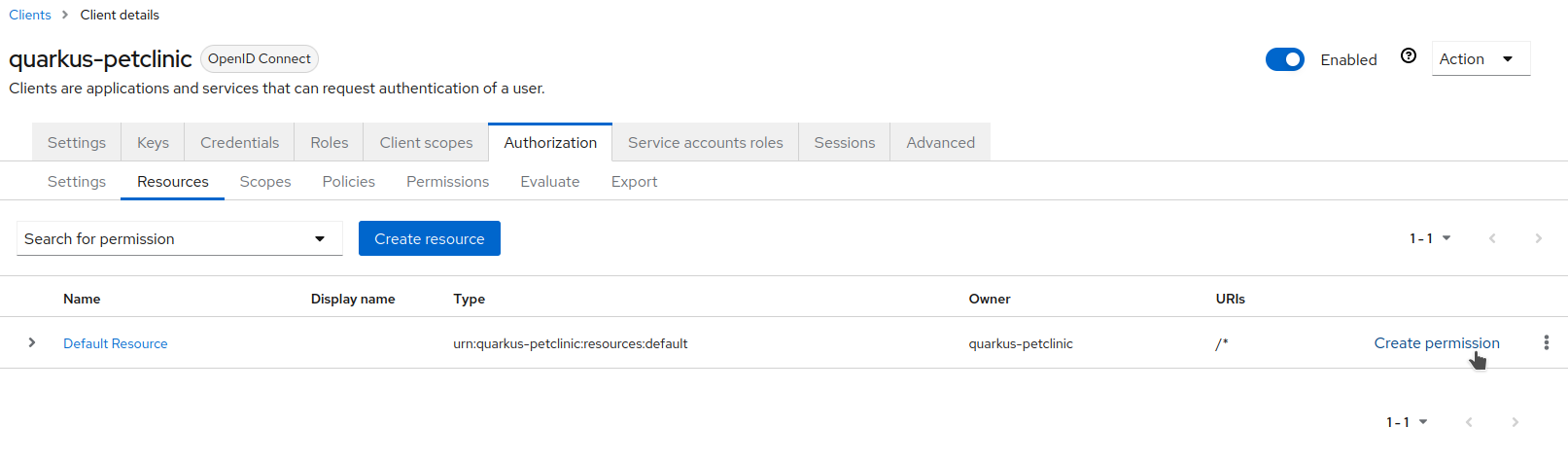
Go back, select the
Resourcestab, and clickCreate permissionfor theDefault Resource.
-
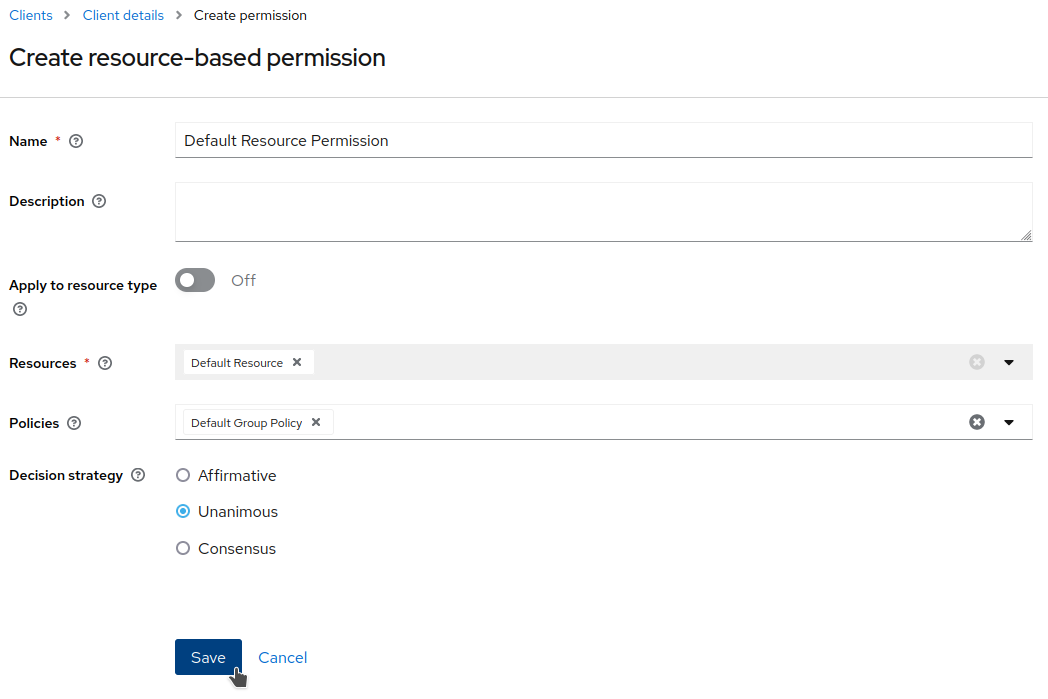
Set
Default Resource Permissionas theNameand selectDefault Resourceas theResource. Add the previously createdDefault Group Policyand clickSave.
-
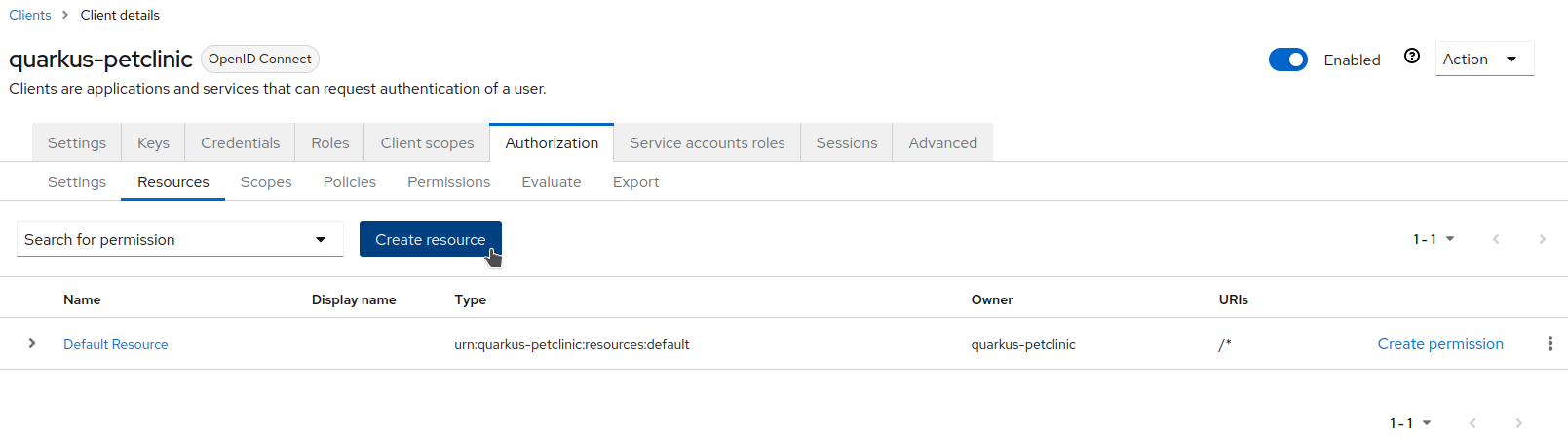
Go back again, select the
Resourcestab, and clickCreate resource.
-
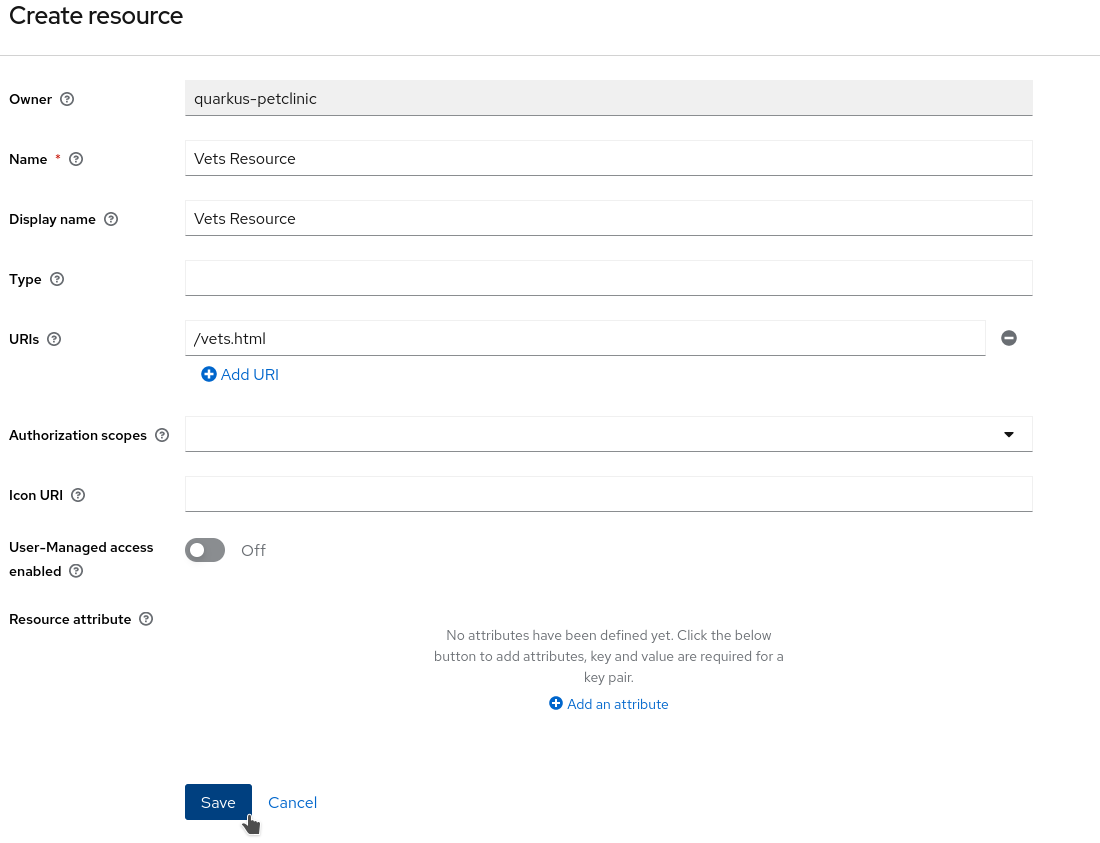
Set
Vets Resourceas both theNameandDisplay name, and/vets.htmlas theURI. ClickSave.
-
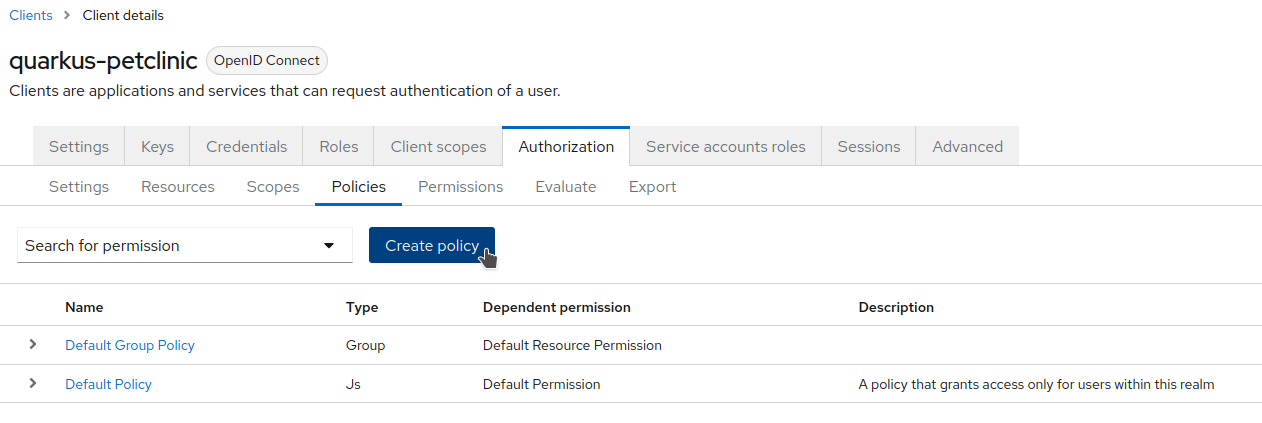
Navigate to the
Authorization→Policiestab and clickCreate policy.
-
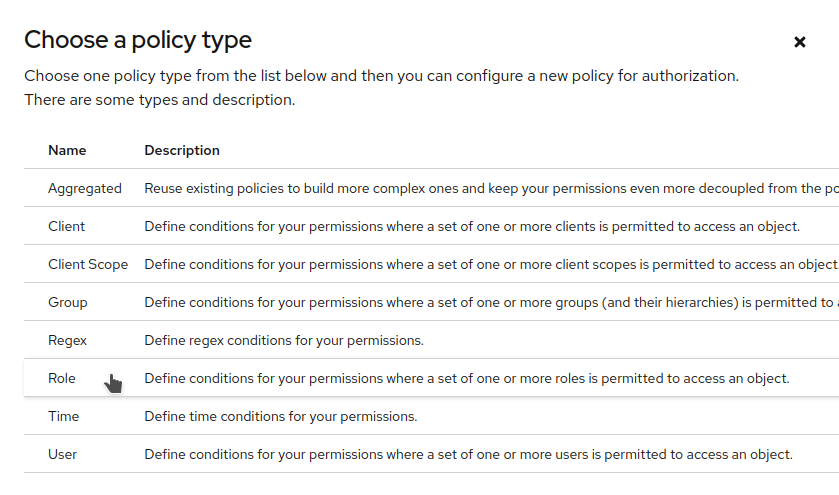
Select
Role.
-
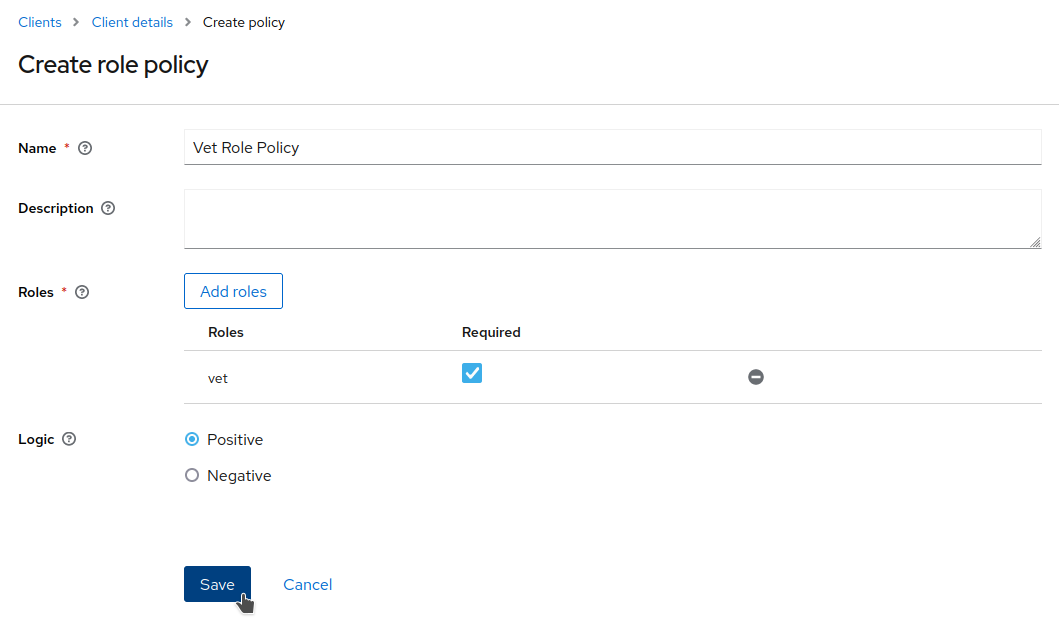
Set
Vet Role Policyas theName, selectvetunderRealm Roles, checkRequired, and clickSave.
-
Navigate to the
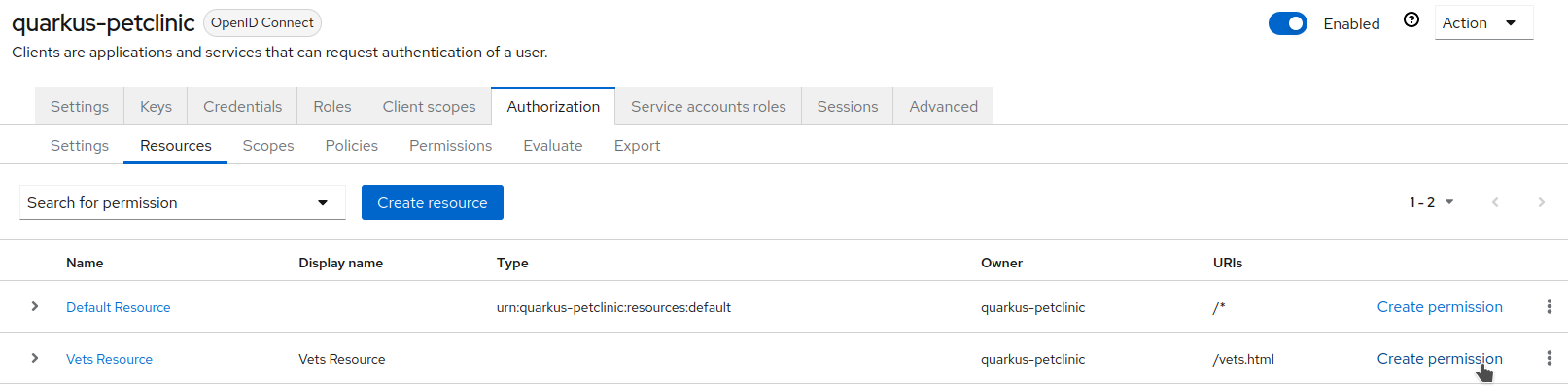
Authorization→Resourcestab. -
Click
Create permissionfor theVets Resource.
-
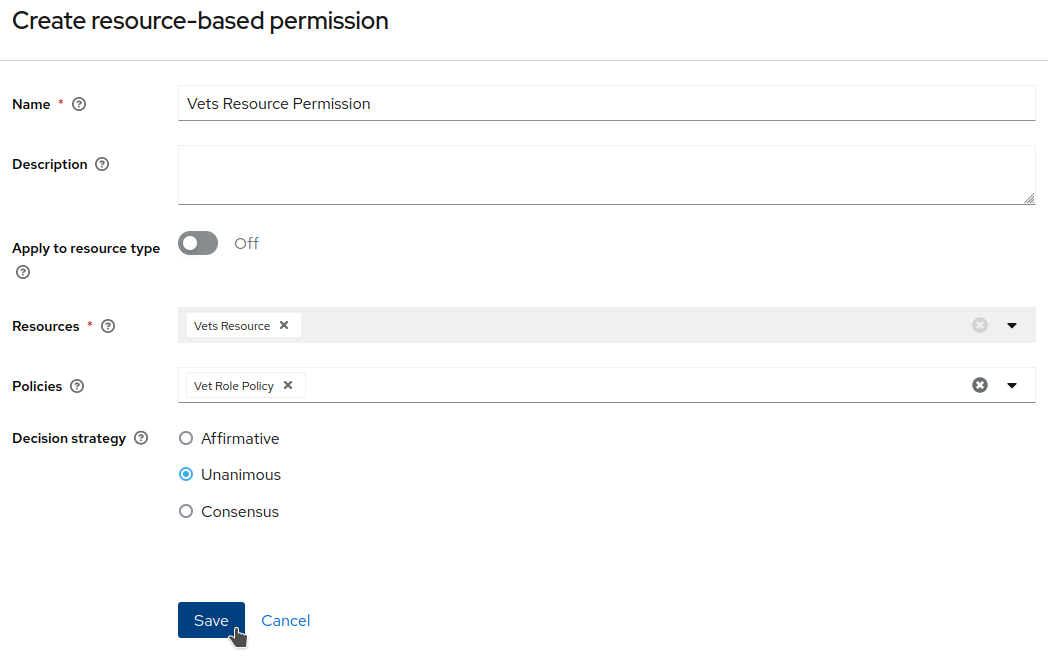
Set
Vets Resource Permissionas theNameand apply theVet Role Policy. ClickSave.
At this point, the Red Hat build of Keycloak client is properly configured.
Let’s configure the application side.
-
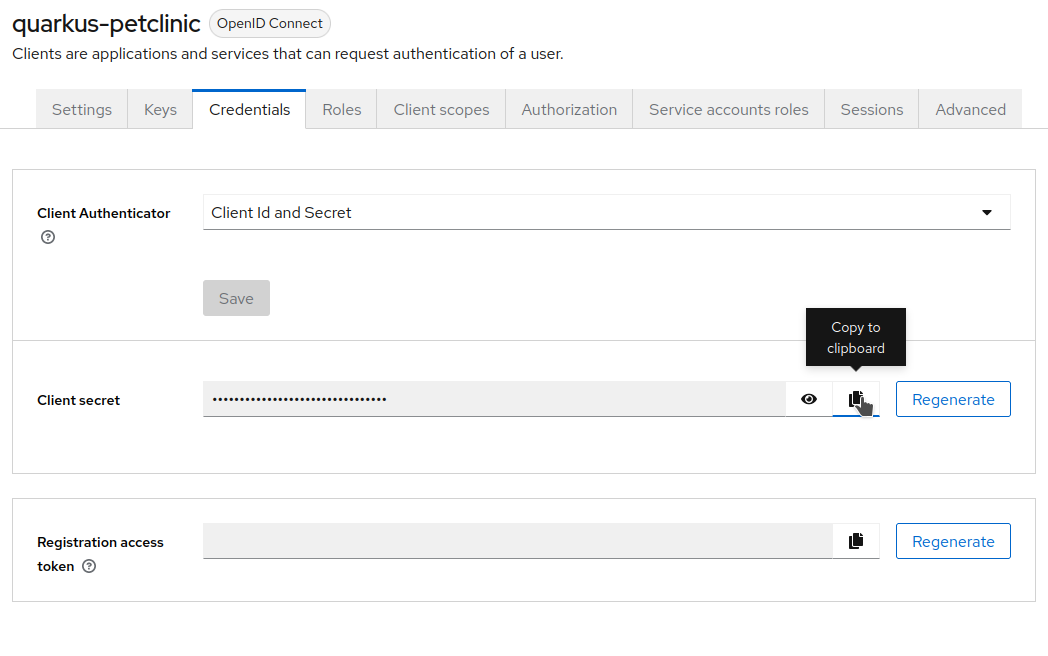
In the Keycloak administration console, browse to the
quarkus-petclinicclient and click theCredentialstab. Write down theSecretvalue — you will need it soon.
-
Export the client secret:
export KEYCLOAK_CLIENT_SECRET=<the secret>-
Add the following dependencies to the
pom.xmlfile:
<dependency>
<groupId>io.quarkus</groupId>
<artifactId>quarkus-oidc</artifactId>
</dependency>
<dependency>
<groupId>io.quarkus</groupId>
<artifactId>quarkus-keycloak-authorization</artifactId>
</dependency>-
Add the following configuration to the application’s
application.propertiesfile:
quarkus.oidc.auth-server-url=http://${KEYCLOAK_HOST:localhost:8080}/realms/demo
quarkus.oidc.client-id=quarkus-petclinic
quarkus.oidc.credentials.secret=${KEYCLOAK_CLIENT_SECRET:secret}
quarkus.oidc.tls.verification=none
quarkus.oidc.roles.source=accesstoken
quarkus.oidc.application-type=web-app
quarkus.oidc.webapp.auth-server-url=${quarkus.oidc.auth-server-url}
quarkus.oidc.webapp.client-id=${quarkus.oidc.client-id}
quarkus.oidc.webapp.credentials.secret=${quarkus.oidc.credentials.secret}
quarkus.oidc.webapp.roles.source=${quarkus.oidc.roles.source}
quarkus.keycloak.policy-enforcer.enable=true-
Redeploy and test the application access:
-
Open a new incognito browser session.
-
Browse to the context root of the Quarkus Petclinic application. The request should be redirected to the Red Hat Single Sign-On login page — confirming that anonymous access is blocked.
-
Log in as
elisabeth. The request will be redirected to the application after a successful login. -
Browse the application and try to access the VETERINARIANS section. Access should be denied since
elisabethhas theassistantrole and this resource is restricted to users with thevetrole. -
Close the browser and open a new incognito session.
-
Visit the context root again.
-
Log in as
angel. -
Browse the application and try to access the VETERINARIANS section. This time, access should be granted since
angelhas thevetrole.
-
A complete OIDC-enabled Quarkus Petclinic application is available in the rhbk-oidc-22 branch.
|