Authentication Cookie Spoofing in OWASP WebGoat
In the realm of cybersecurity and web application development, projects like OWASP WebGoat play a pivotal role in enhancing our understanding of vulnerabilities and security best practices. As a dedicated contributor to the OWASP WebGoat project, I have taken on the responsibility of implementing and reinvigorating various scenarios, breathing new life into lessons from earlier versions of the platform. In this pursuit, I have focused my efforts on revamping the authentication cookie spoofing scenario —a crucial component in the arsenal of web security education. By reimagining and enhancing this challenge, I aim to provide learners with an enriched and contemporary learning experience that reflects the ever-evolving landscape of web application security.
In this article, the spotlight falls on the intriguing realm of authentication cookie spoofing. This technique involves exploiting vulnerabilities within a web application to impersonate a legitimate user by manipulating authentication cookies. By understanding the mechanics of this attack vector, developers and security enthusiasts can better comprehend the nuances of safeguarding user sessions and preventing unauthorized access.
It’s important to note that a wealth of resources is already available to guide individuals through the process of solving this lesson. Some of these resources are:
[A1] Spoofing an Authentication Cookie - WebGoat
Web Security Unmasked: Spoofing Authentication Cookies - A Satirical Tutorial
My goal is to provide additional details and discuss how the lesson has been implemented, offering specific technical insights into the decisions made, the challenges encountered, the didactic point of view, and, of course, the solution that I consistently incorporate in my implementations— one that remains technology-agnostic.
Deciphering the Authentication Cookie: An Introduction
Authentication cookies, often referred to simply as “auth cookies,” serve as essential components within the realm of web application security. These small pieces of data are generated and assigned by a web server to uniquely identify and validate users during their interaction with an application. Operating as a form of digital identification, authentication cookies are bestowed upon users upon successful login, allowing them to access restricted areas or perform actions tailored to their privileges. These cookies, typically encrypted to safeguard sensitive information, play a pivotal role in maintaining a seamless and secure user experience by eliminating the need for users to repeatedly provide their credentials throughout their session.
A session represents a logical connection between a user and the web server, enabling the application to recognize and track the user’s activities across different pages and interactions.
Authentication cookies play a crucial role in establishing and maintaining sessions. When a user successfully logs in, the web server generates a unique session identifier, often referred to as a session ID. This identifier is then stored within an authentication cookie on the user’s device. Subsequently, as the user navigates through the application, their actions and preferences are associated with this session ID, allowing the server to retrieve and restore relevant data.
In essence, the authentication cookie acts as a key that links the user’s current session with their identity. The session ID stored within the cookie serves as a reference point for the server to access the user’s session data, which may include variables, preferences, and temporary data pertinent to the user’s activities.
From one perspective, housing the cookie on the user’s device exposes it to potential vulnerabilities, making it susceptible to theft through the exploitation of certain weaknesses or interception via man-in-the-middle attacks or cross-site scripting (XSS). Simultaneously, if the algorithm responsible for cookie generation is compromised, the values within the cookie could be deduced.
In numerous instances, applications are designed to initiate an automatic user login upon the provision of the appropriate authentication cookie.
Decoding and Unraveling: A Comprehensive Exploration
The aim is to decipher the methodology behind cookie creation, enabling the attacker to replicate and generate the cookie from their end. This exploitation grants unauthorized access, allowing the attacker to effectively masquerade as a legitimate user and gain unauthorized entry by harnessing the power of the compromised cookie.
The lesson presents a login panel that prompts for a username and password. The authentication process follows this lifecycle: if the page receives a valid “spoof_auth” cookie, the system automatically logs in the user. If the request lacks a cookie but the provided credentials are accurate, the system generates a new “spoof_auth” cookie. Otherwise, access is denied. Our objective is to successfully log in with the user “Tom,” without, of course, possessing knowledge of his credentials.
We proceed to attempt a login with one of the users provided in the prompt, and observe the following:
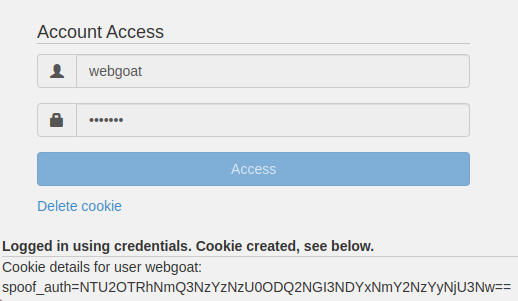
As we can readily observe, the cookie value is encoded in base64. Upon decoding this value, it becomes apparent that it is further encoded in hexadecimal.
echo NjM3OTRhNGY0ODRiNTQ0OTU3NDU3NDYxNmY2NzYyNjU3Nw== | base64 -d
63794a4f484b5449574574616f67626577
echo 63794a4f484b5449574574616f67626577 | xxd -p -r
cyJOHKTIWEtaogbew
Upon subsequent decoding, a text string emerges, which is notably intuitive, the user name is discernible, accompanied by appended random text. Upon requesting additional cookies for the same user, it becomes evident that the cookie generation process involves concatenating ten characters of randomness (salt) with the user name.
This amalgam is then subjected to a reversal (webgoatEWITKHOJyc), followed by encoding in both hexadecimal and base64 formats.
Forging the Key: Exploiting the Crafted Cookie for Unauthorized Access
Let’s delve into the process of crafting an authentication cookie for Tom.
Our initial string will consist of the username followed by a ten-character random text. Subsequently, we reverse this string.
tomAAAAAAAAAA → AAAAAAAAAAmot
Next, we encode it in hexadecimal and then convert it to base64.
# warn: do not encode any whitespace or newline character
echo -n AAAAAAAAAAmot | xxd -ps
414141414141414141416d6f74
# warn: do not encode any whitespace or newline character
echo -n 414141414141414141416d6f74 | base64
NDE0MTQxNDE0MTQxNDE0MTQxNDE2ZDZmNzQ=
If we send this value as a cookie, we will have successfully logged into the system as the user Tom.

Implementation Insights: Final Recommendations for a Safe Approach
The implementation of a weak encryption method for encoding session cookies exposes the system to inherent vulnerabilities, rendering it susceptible to unauthorized breaches. This lack of encryption strength jeopardizes data privacy and compromises the integrity of user credentials, creating a fertile ground for malicious attacks. Robust encryption serves as a stalwart guardian against these threats, forming an indispensable shield to safeguard sensitive information and fortify the system’s resilience against potential intrusions.
However, the pitfalls of manually crafting secure cookie values cannot be overlooked. The intricate nuances of encryption and secure session management demand a meticulous approach that goes beyond ad hoc implementations. In this context, the strategic adoption of established frameworks and libraries emerges as a potent strategy. These purpose-built tools come armed with cutting-edge encryption techniques, orchestrating the complexities of authentication and session handling behind the scenes. By embracing these well-engineered solutions, developers not only endorse industry best practices but also shield their applications from potential vulnerabilities that often accompany manual endeavors. This shift from manual to framework-driven implementation marks a pivotal step towards bolstering the resilience of systems against a multitude of security threats.